Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- Re: how to forward a msg to email/slack trigger al...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how to forward a msg to email/slack trigger alert
Hello,
I'm trying to add msg value to slack and email trigger alert but I'm getting the first word of msg field.
I would like to get the full message.
here's the search results:
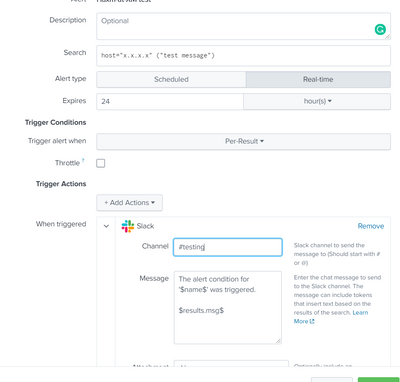
here's the slack trigger: I used $results.msg$
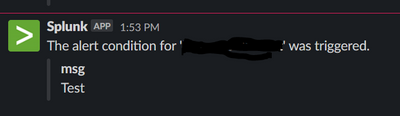
this is what I get:
now, I want to get the full message.
instead of "Test", I want to forward the full message from msg field: "Test message generated successfully"
could you please assist?
Thanks,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It doesn't seem to take the msg field but the literal "msg" from your token.
Use $result.msg$ instead of $results.msg$
Please be reminded that the filed values are limited to first value for the specified field name from the first search result row. Also make sure that the field is available(fields a,b,c,) in the result set especially if its an extracted field
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@renjith_nair , I've changed to $result.msg$ but still, it presents only the first word.
maybe there are other ways to get the full message instead of the first word?
Thanks,
Dan
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@danan, in your screen shot (between host and sourcetype), it extracts "Test" as a value in msg. You shall try adding quotes around the message to treat them as a single field , e.g. "Test message generated ....".
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@renjith_nair , Thanks! how do i do this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's easy if you could change in the data inputs/ingest time. Just add quotes around the value before its pushed to Splunk.
For those events which are already available in Splunk, you may extract it from _raw
e.g.
|rex "msg=(?<message>.+)"
What goes around comes around. If it helps, hit it with Karma 🙂