Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- Re: Triger Alert For High Number of Failed Login W...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm new to Splunk Enterprise, I want to trigger a real-time alert if failed attempt login is more than 3 times every or within 5 minutes, for example, 01:00 PM until 01:05 PM there is a failed login attempt more than 3 times, so alert will show.
this is my question:
A. What is the best type of alert for this case? Real-time rolling window ? or Real-time per result?
B. What is the best practice to specify the trigger condition for this case (according to question A)? Is it in search command? Or in alert form custom trigger condition?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay, so what I understand is scheduled alert doesn't have time to start the alert, right?
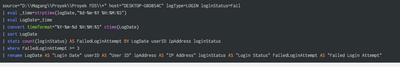
The search I fixed:
The cron schedule I fixed:
Is it good to go already?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @mathiasy123 ,
I don't hint to use a real time alert because it uses many resources and it's usually non mandatory to have a real time alert when the following intervene is human!
If you want to monitor a Windows system, you can check the EventCode=4625 and define the threeshold you want for the monitoring period, e.g. something like this:
index=wineventlog EventCode=4625 earliest=3m latest=now
| stats count BY host Account_name
| where count>3in this way you have a search that has results when you have more than 3 logfail in the last 3 minutes.
You can schedule it using this cron (every three minutes):
*/3 * * * *Answering to your questions:
A) don't use a real time search!
B) you have to create the above search and save it as an alert, specifying the other informations (frequency, actions, etc...).
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually, I want to detect a failed login attempt on payment gateway transaction, for the sake of testing, I set if every 3 minutes user has more than 3 times failed login, it may be an anomaly and the alert will show.
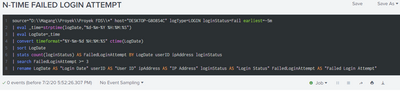
According to your answer, this is my search then:
And this is my corn schedule:
Is it correct?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @mathiasy123 ,
only two little updates:
- in your search use where instead search in the threeshold condition;
- if you want to run your alert avery 5 minutes, you have to modify the cron espression that is setted to 3 minutes.
In addition, you don't need to insert earliest and latest in the main search if you configure the monitoring tie period in the alert panel.
Then, I always use the index=xxx filter because the search is faster.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, @gcusello
Here my response:
A. Can you let me know, why use where command instead of search command? Because the Splunk always suggest me to use the search command from the pop-up suggestion.
B. How can I set the scheduled alert start time? Let say, I want to set the alert start at 09:00 AM every day.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @mathiasy123 ,
I usually use where for simple filters like your, probably the suggest of search is because you used it more times.
Here you can find an interesting answer to your question: https://community.splunk.com/t5/Splunk-Search/What-s-the-difference-between-where-and-search-in-the-...
About scheduling, I understood that you wanted a real time monitoring, for this reason I hinted (to a near real time monitoring) to use an alert scheduled every 5 minutes, not once a day.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay, so what I understand is scheduled alert doesn't have time to start the alert, right?
The search I fixed:
The cron schedule I fixed:
Is it good to go already?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're welcome!
Ciao and next time!
Giuseppe
P.S.: Karma points are appreciated 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Alright, I'll let you know if the problem occurs again!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can use normal scheduled search for this use case. Real time searches comes with its on drawback w.r.t resource utilization. Have a look at some of the community discussions about this topic - https://community.splunk.com/t5/Splunk-Search/Why-are-realtime-searches-disliked-in-the-Splunk-world...
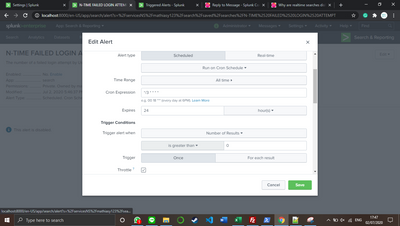
Regarding trigger conditions, it depends on your organization practices. However, if you are specifying the trigger conditions in your alert configuration, you might be able to use the same search in other places such as dashboards or summary index etc.
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
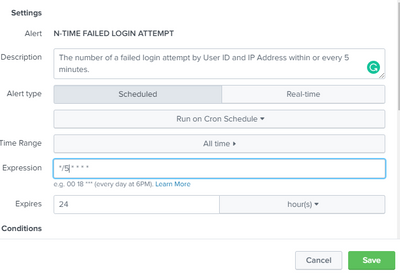
Okay, so I can use the scheduled search with cron style like:
*/5 * * * *
Is it correct?
And how to set the alert start time?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you can mention the alert start time in the search using earliest=-5m
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah I see, I read about earliest in the documentation but I haven't fully understood what the mean really is, so earliest=-5m means the schedule alert start before 5 minutes?
And do I need to define the latest?