Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- Splunk Alerting
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk Alerting
Hi,
I would like to understand how I would be able to setup an alert that must be sent via email only once. Eg. When an event is returned for a search an alert is raised an an email gets sent. I only want to be notified once about this event. In other words if the search runs every 5 minutes it should send the alert for the initial event it picks up, not every 5 minutes.
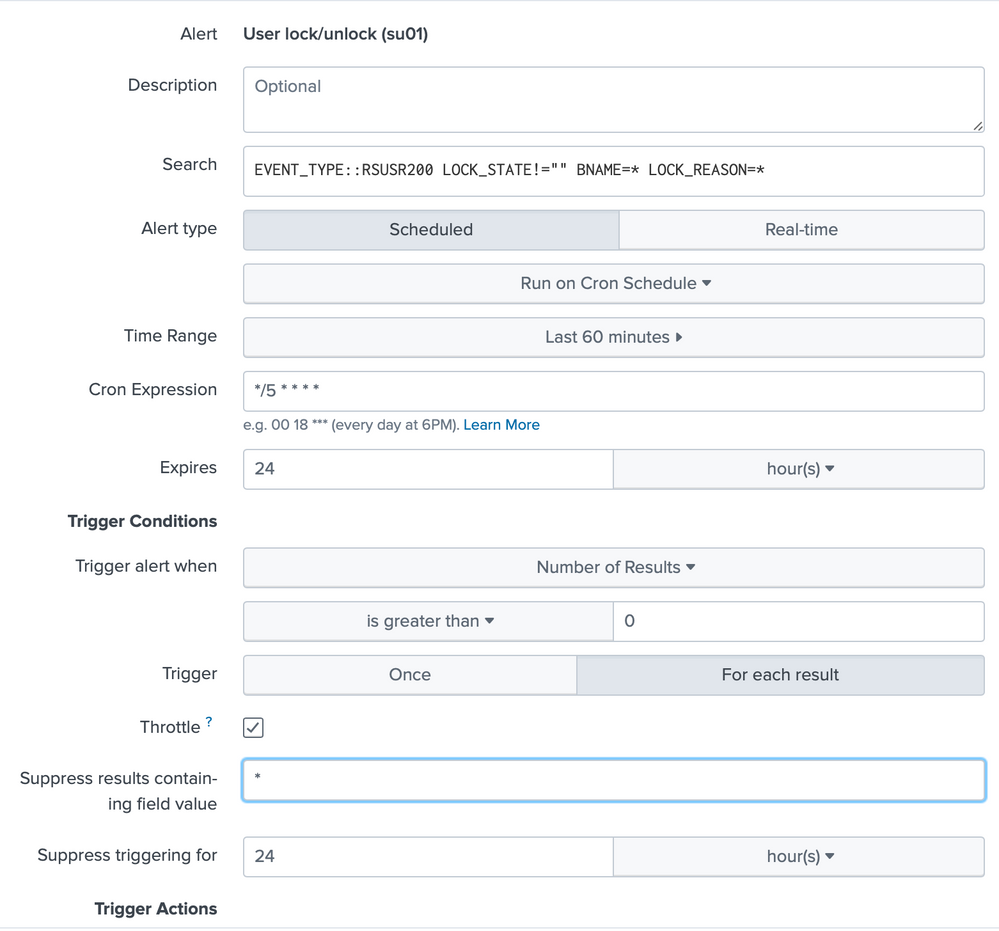
Is the only way to prevent this by selecting Throttle and specifying a number of hours/days/minutes to suppress the alerts?
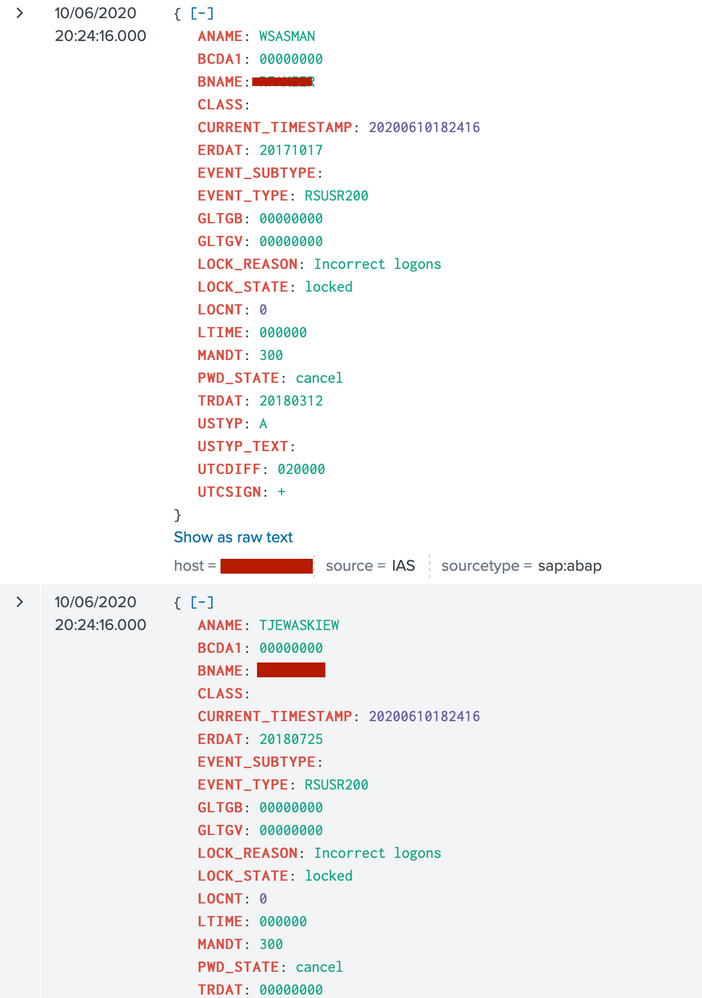
In my search example I receive the usernames that are locked out with times etc in a table format. I am worried that if I set suppress I will not receive new locked out usernames during that period.
So basically I only want an email event sent once, and only again when the search result changes from the initial result, but still conforms to the conditions setup in the alert.
I hope this makes sense and if someone could assist me in understanding what I can do.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Throttling will control how often the email is sent. You will need to craft your search so that it detects new lockout events during the time range. Then you can set the alert criteria to alert if the returned event count > 0.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, I've tried that but it doesnt seem to work. Maybe it's related to the search query? Basically there are 2 events that show up every hour (polling cycle seems to be 60 minutes for these events).
I need the initial event that shows those 2 events, and then only again if there is a new entry/event with a different user.
See attached screenshots of search and alert settings. I have set it to supress for 24 hours for now just to stop the alerts continuously being emailed.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe create a lookup of user ids that have been found as locked (with the date time found) and then when you find a user do a lookup match and only return events where the user isn't in the lookup and as a final step update the lookup with new users.