- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- Splunk Alert Throttle - Logically AND/OR?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
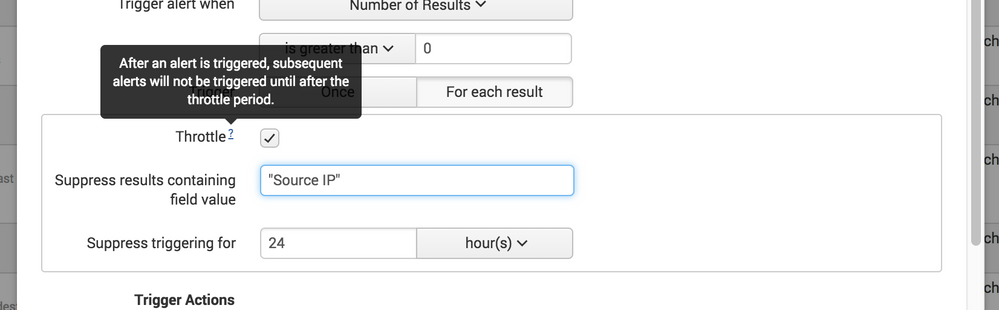
When adding multiple fields in the "Suppress results containing field value" - is that logically an AND or an OR? This could produce two entirely different outcomes. I would ideally like to suppress when both fields are found in subsequent alerts, however, it seems like this might say for any future alert that contains either field, don't alert again. Some clarity would be nice! (The documentation doesn't touch on this)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I submitted doc feedback for you earlier today and here is the response I received.
The “Per-result” option depends on the value of fields you specify. It works as an AND. So, for example:
If you have two fields, say “userID” and “URL,” specified in your search, and the search you run returns events where logins failed, say the value is “FAILED”. If you specify “userID” and “URL” in your throttle, an alert will not trigger if those two field values are returned as “FAILED”. It will alert if only one field returns as “FAILED” but the other returns a different value.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I submitted doc feedback for you earlier today and here is the response I received.
The “Per-result” option depends on the value of fields you specify. It works as an AND. So, for example:
If you have two fields, say “userID” and “URL,” specified in your search, and the search you run returns events where logins failed, say the value is “FAILED”. If you specify “userID” and “URL” in your throttle, an alert will not trigger if those two field values are returned as “FAILED”. It will alert if only one field returns as “FAILED” but the other returns a different value.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the documentation is ever unclear about something, submit feedback at the bottom of the on-line documentation page. Splunk's docs team is excellent about updating the documentation in response to user feedback.
If this reply helps you, Karma would be appreciated.