Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- Phone Home Error Not Alerting Properly
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
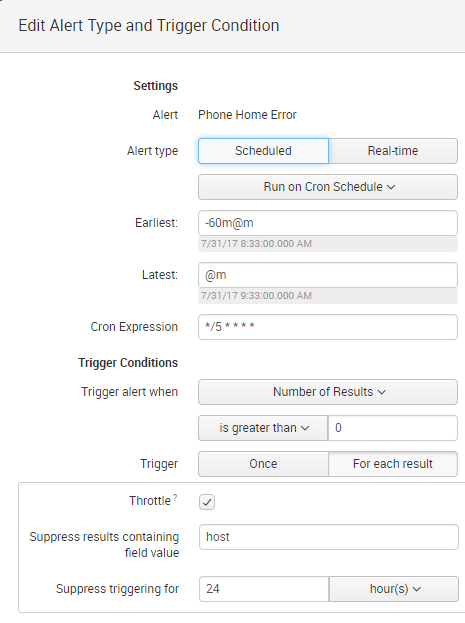
So, I have my Phone Home Error search; when I type it into the Search Bar, it pulls up all hosts not connected. However, when I try to set it up as an alert, it will only send out an Alert for the first one that disconnected. I have it Throttled, but for suppressing those with the same host.
Also, over time, it will stop pulling computers that have been disconnected from the server for more than 7 days. The only way to get them is to do an All Time search (using the search string from the alert).
I'm a little lost, and would be thankful for any guidance. Thanks.
My Search:
| metadata type=hosts index=_internal | eval age=now()-recentTime | where age > 300 | eval "Time Indexed"=strftime(_time, "%Y/%d/%m %H:%M") | eval "Computer Host"=host | eval "Time Last Connected"=tostring(age, "duration") | eval "Date Last Connected"=strftime=)recentTime, ""%+") | table "Computer Host", "Time Last Connected", "Date Last Connected"
My Alert Settings:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Generally, when using the metadata command for something like this, you should be using All time for your search span. The way that metadata works is to go to buckets written within your span and give you a summary of that If you limit your search's time to a window that does not include any buckets, then you will get no summary, which is NOT what you need. So set it to All time (or a REALLY long time) and do not at all be concerned that you are doing a deep/expensive search, because for this particular command, you definitely are not because like tstats, it is operating on the metadata.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Generally, when using the metadata command for something like this, you should be using All time for your search span. The way that metadata works is to go to buckets written within your span and give you a summary of that If you limit your search's time to a window that does not include any buckets, then you will get no summary, which is NOT what you need. So set it to All time (or a REALLY long time) and do not at all be concerned that you are doing a deep/expensive search, because for this particular command, you definitely are not because like tstats, it is operating on the metadata.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suppose I misunderstood what metadata is used for. Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try to change query like below,
| inputlookup dmc_forwarder_assets
| search status="missing" AND os="Windows"
| fields hostname os arch forwarder_type version last_connected status
| rename hostname as Instance
| eval now=now() | eval Duration_Not_Connected=now-last_connected | where Duration_Not_Connected<=2592000 | fields - last_connected now | sort Duration_Not_Connected | eval Duration_Not_Connected_Days = round(Duration_Not_Connected/86400,0)