Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- Re: Windows process monitoring Alert
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to create a Windows process monitoring alert?
I am looking for a Alert query for monitoring the windows process
below is the scenario
1. Lookup having a field name called "host" and "Process"
2. windows index query where the process gets updating in the field called "Name" and we have host field as well by default.
3. Query needs to pick the value from the "host" and "Process" from the lookup and finds the matching in the windows based index query, events should generate in Splunk results
Kindly assist.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
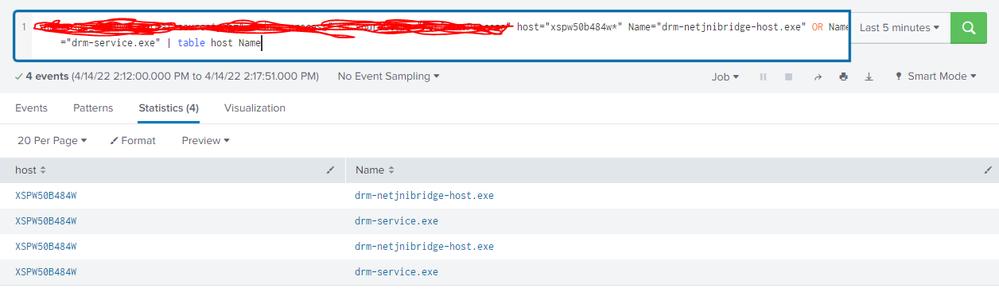
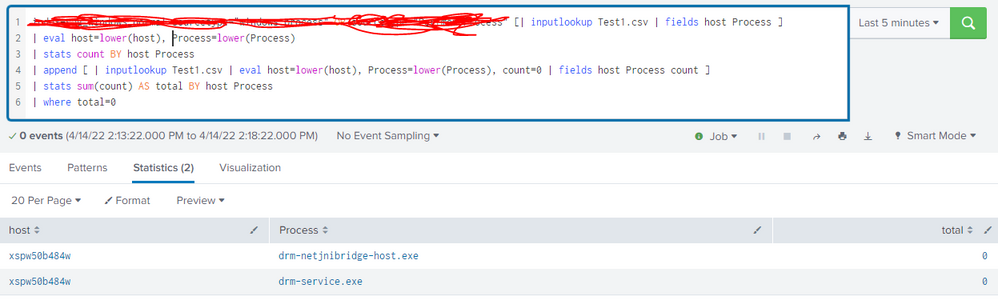
Hi @gcusello
Please find below 2 results where lookup query still showing count as 0 though the process returning events while running for index query alone
Events related search from index
process query using lookup that shows count=0
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello - any suggestions as we still not able to crack it
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
what does it happen if you run only the first three rows (until the first stats)?
in you results, have you "drm-netjnibridge-host.exe" and "drm-service.exe"?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
As I supposed, the problem is in the main search, there are two choices:
- in the main search (the one you maskered) or in the lookup (or in both) there isn't one or both the fields "host" and "Process" (beware that field names are case sensitive!),
- there isn't any common pair host/Process between the main search and the lookup;
so there isn't any result to the main search.
So at first run the above search (the first three rows) without the subsearch and see if you have results.
If not, the problem is in the field names and you have to check them.
If yes, see the result pairs and see if there's someone of them in the lookup.
In this case you have to debug this situation before starting the analysis of the missing processes.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it should return host and Process results if the values from the lookup isn't coming/occurring as events through index
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
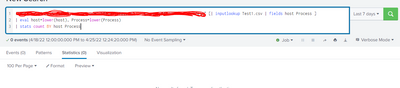
Hi @sureshkumaar,
if the Process name in the lookup is the same of the Process field in events, you could use something like this:
index=your_index NOT [| inputlookup your_lookup.csv | fields host Process ]
| ...Ciao.
Giuseppe