Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- How to create a Windows process monitoring alert?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to create a Windows process monitoring alert?
I am looking for a Alert query for monitoring the windows process
below is the scenario
1. Lookup having a field name called "host" and "Process"
2. windows index query where the process gets updating in the field called "Name" and we have host field as well by default.
3. Query needs to pick the value from the "host" and "Process" from the lookup and finds the matching in the windows based index query, events should generate in Splunk results
Kindly assist.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello - i am getting the process names that aren't in the lookup also, where as i am looking only when both process name in lookup and index is matching
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
sorry I forgot a part of the search, please try this:
index=your_index [| inputlookup your_lookup.csv | fields host Process ]
| eval host=lower(host), Process=lower(Process)
| stats count BY host Process
| append [ | inputlookup your_Process_Lookup.csv | eval host=lower(host), Process=lower(Process), count=0 | fields | eval host Process count ]
| stats sum(count) AS total BY host Process
| where total=0In this way you monitor all the processes in your systems but only the ones listed in the lookup.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello
getting error while trying to execute it
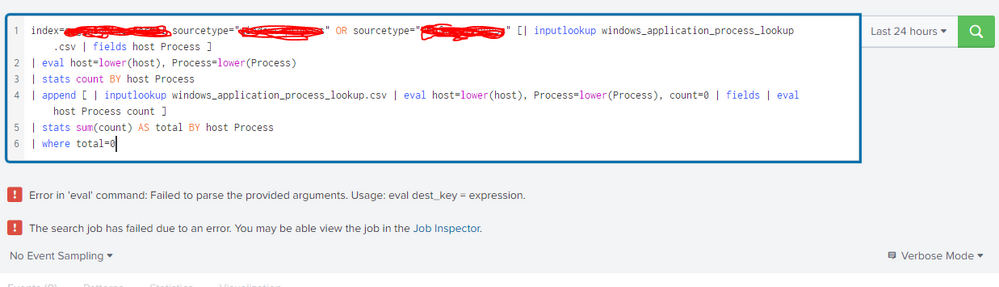
Error in 'eval' command: Failed to parse the provided arguments. Usage: eval dest_key = expression.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
are you sure that you used the comma between the two expressions like my sample?
Could you share your search?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
I understand that your query is picking the values from one lookup and appending to another lookup
but actually my requirement, Splunk should show events when the values of host and process matches from one specific LOOKUP table when it matches with values of host and process which comes from the index query it should give the value
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
my approach is related to the requirement to find the processes that aren't present in the events.
using my search you have the count of events for each present process then you add one entry for each process that should be present, in this way you have a value=0 when in your lookup there a process for an host without events.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello
I have these many fields in the lookup "windows_process"
host Process ResolutionID Assignment_Team Escalation_Team Urgency autocloser CI Attribute
Is there any way to pick the value of "host" and "Process" from the lookup and match with values of "host" and "Process" which comes from the index=windows sourcetype=process?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
please try this:
index=windows sourcetype=process [| inputlookup windows_proscess | fields host Process ]
| eval host=lower(host), Process=lower(Process)
| stats count BY host Process
| append [ | inputlookup your_Process_Lookup.csv | eval host=lower(host), Process=lower(Process), count=0 | fields | eval host Process count ]
| stats sum(count) AS total BY host Process
| where total=0Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
From the query you provided, in the look where this inputlookup is mentioned, can you please let me know do we need to create an empty lookup with host, Process and count fields? where the values gets captured from index and the existing lookup windows_proscess?
| inputlookup your_Process_Lookup.csv
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
as you said, you already should have the lookup "windows_process" containing at least two columns (the other columns aren't relevant for the check).
You need this lookup to have a perimeter to check, but you said that youalready have it.
In my search you can use it adding a value for the check, but it isn't a column of your lookup, to use only for the check.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello - Please find the snapshot where i am getting error using same lookup name in both the inputlookup
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
sorry cut & past error!
please try this:
index=windows sourcetype=process [| inputlookup windows_proscess | fields host Process ]
| eval host=lower(host), Process=lower(Process)
| stats count BY host Process
| append [ | inputlookup your_Process_Lookup.csv | eval host=lower(host), Process=lower(Process), count=0 | fields host Process count ]
| stats sum(count) AS total BY host Process
| where total=0Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello
Thanks for providing the query, i believe this query will show the results for all the process matching with lookup and index based process events.
Can we modify this query a little bit and see where we can see if the process from the lookup isn't coming in the index based process?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
as I said, I would show you the approach so you can adapt my hint to your real needs!
tell me if I can help you more, otherwise, please, accept one answer for the other people of Community.
Good luck and happy splunking.
Ciao.
Giuseppe
P.S.: Karma Points are appreciated by all the Contributors 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
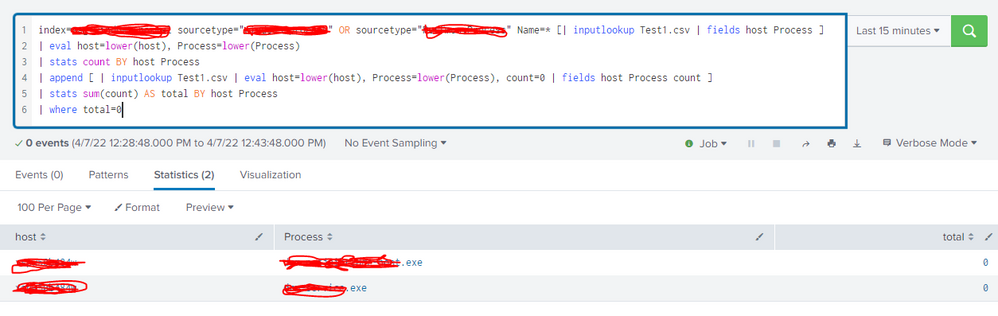
Hi @gcusello
To test the query, i created one sample lookup "Test1.csv" and added only 2 entries and when i run the query those 2 entries are getting displayed in the result.
Where as it shouldn't get displayed in the results for this query as those 2 processes are sending events to the index
Process gets updated in lookup table field called "Process"
in Index process name gets updated in the field called "Name"
when these 2 matches we shouldn't be seeing the results, but we are seeing results
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
it's correct: in this way you found the pair host/Process present in lookup and not present in main search results, in other words missed.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello
But in the INDEX query we are able to the see process related events returning.
And my doubt here is the process name is getting updated in the field called "Name" in the INDEX based query
how it is able to check and match the name which is in the lookup ("Process") field?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
yoiu have to maintain the lookup, you can do it manually or running a simple search with outputlookup.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
Query isn't working fine
But still the results are returning from lookup, even though process is up and running fine
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @sureshkumaar,
if there are pairs host/process from the lookup that have in the search results count=0 but for the same pair there are events, thismeans that there something different, maybe in the names there's something different.
Colud you share some pairs thet have count=o0 in the search and the corrispective that have events?
Ciao.
Giuseppe