Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Alerting
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- Re: Creating an alert to find fail login within 15...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Creating an alert to find fail login within 15 minutes with a hit of higher than 3 times?
normangoh
Explorer
06-16-2015
06:26 AM
Hi guys,
I need to create this alert that will fetch failed logins that happen more than 3 times within 15 minutes and display the results as user and the number of events per that user.
I am thinking using something like:
index=indexName eventtype="failed_logins" | bucket _time span=15m
or
index=indexName eventtype="failed_logins" | tranactions <something?> maxspan=15m
Anyone experts can give me some guide?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
stephanefotso
Motivator
06-16-2015
06:50 AM
Hello! Here you go
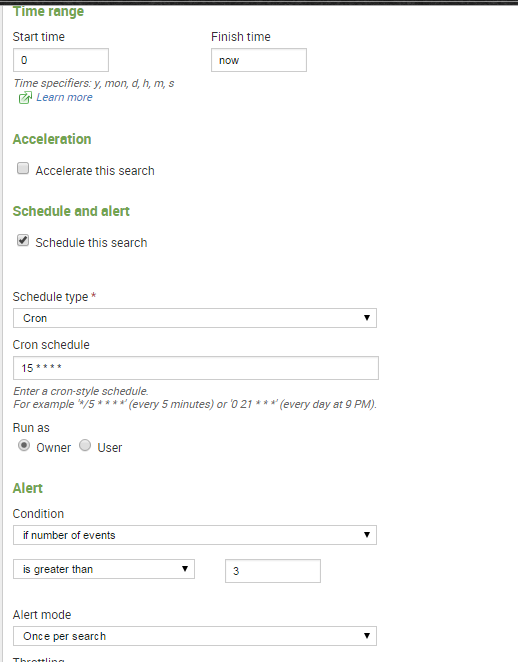
index=indexName eventtype="failed_logins" |stats count
Save it as an Alert!
Title: Failed_alert
Alert Type: Real Time
Trigger Condition: Number of Results
Trigger if Number of Results is : Greater than 3
in : 15 min
For more information, Read here :http://docs.splunk.com/Documentation/Splunk/6.2.3/Alert/Definerolling-windowalerts
Thanks
SGF
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gyslainlatsa
Motivator
06-16-2015
06:48 AM
hi normangoh,
write your query
index=indexName eventtype="failed_logins"
and backup simply as an alert with the following characteristics:
when your research to see all the results, you can use the following query:
index = indexName eventType = "failed_logins" user = * |table user _raw
Get Updates on the Splunk Community!
Splunk Decoded: Service Maps vs Service Analyzer Tree View vs Flow Maps
It’s Monday morning, and your phone is buzzing with alert escalations – your customer-facing portal is running ...
What’s New in Splunk Observability – September 2025
What's NewWe are excited to announce the latest enhancements to Splunk Observability, designed to help ITOps ...
Fun with Regular Expression - multiples of nine
Fun with Regular Expression - multiples of nineThis challenge was first posted on Slack #regex channel ...