Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- Re: Alerts searching for statistics - not events
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Team,
I have a search which is returning statistics (not events).
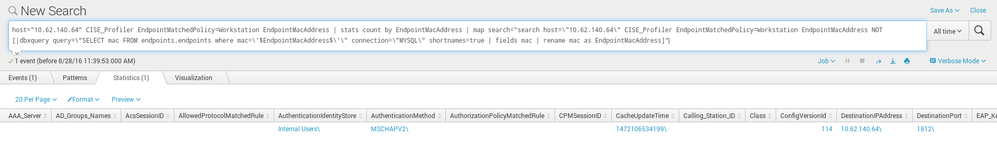
I would like to generate alert and call custome bash script only in case where i have at least 1 statistic result like this:
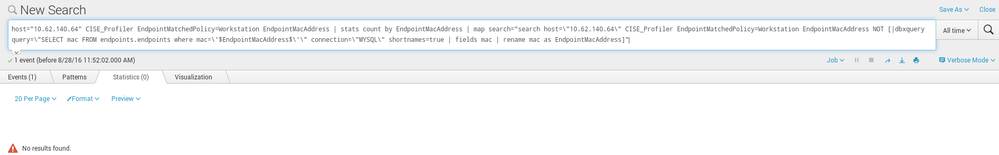
While i do not want to call external script when having 0 statistic results like this:
Please keep in mind that for both we do have 1 event found - and that is irrelevant.
I have read:
http://docs.splunk.com/Documentation/Splunk/6.4.3/Alert/Configuringalertsinsavedsearches.conf
And can see: "Alerts use a saved search to look for events". But in my case i am not interested in events but statistics.
Possible ?
How to launch external script easily in case i have a match and statistic data is produced ?
Thanks,
Michal
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Save the search as an alert, set the alert to trigger when there is more than zero results, and have the alert call your external script as an alert action.
I'd recommend doing that through the UI, but if you want to use savedsearches.conf directly these are some relevant settings:
http://docs.splunk.com/Documentation/Splunk/6.4.3/admin/savedsearchesconf#Notification_options - the value might be "number of events", but it's actually triggering based on number of results
http://docs.splunk.com/Documentation/Splunk/6.4.3/admin/savedsearchesconf#Settings_for_script_action
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Save the search as an alert, set the alert to trigger when there is more than zero results, and have the alert call your external script as an alert action.
I'd recommend doing that through the UI, but if you want to use savedsearches.conf directly these are some relevant settings:
http://docs.splunk.com/Documentation/Splunk/6.4.3/admin/savedsearchesconf#Notification_options - the value might be "number of events", but it's actually triggering based on number of results
http://docs.splunk.com/Documentation/Splunk/6.4.3/admin/savedsearchesconf#Settings_for_script_action
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk Free doesn't have alerting.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Martin,
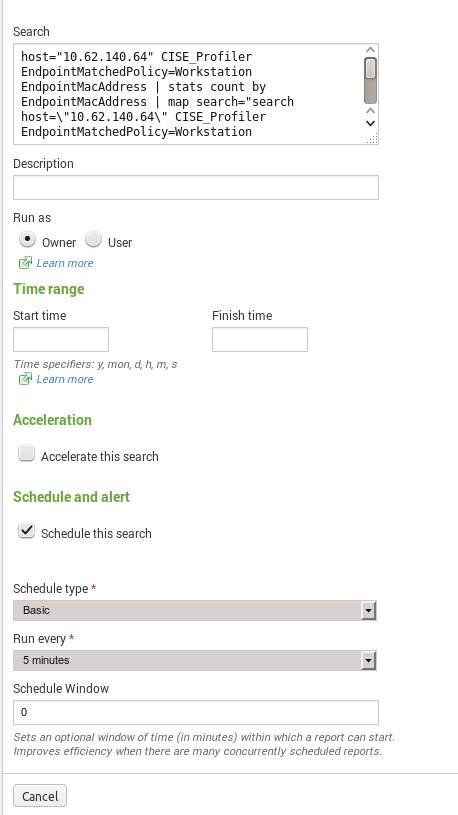
I do not see that option in UI, is that possible because of the fact that i have free/trial version in the lab ?
(while full/entrprise in the production) ?
Can i still do it via conf files in CLI ?
Thanks,