- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why splunk Search returning duplicates?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why splunk Search returning duplicates?
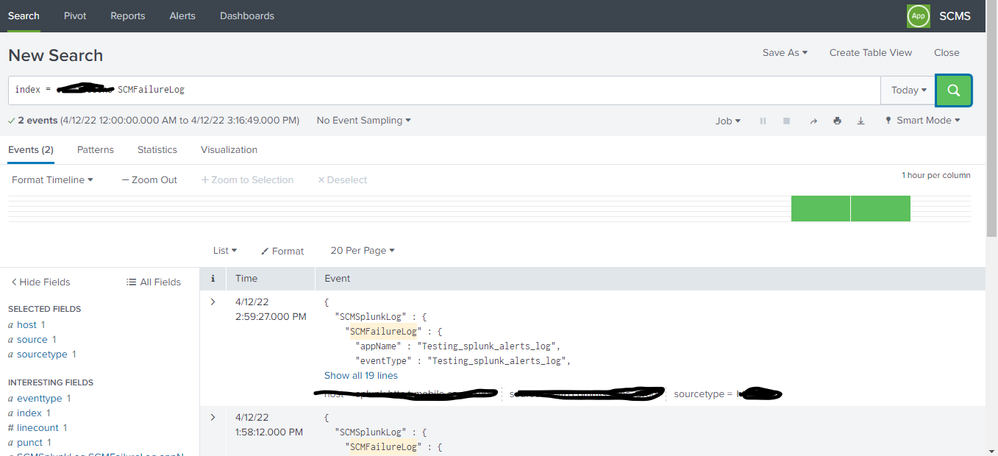
As shown below I have only two events present on my index
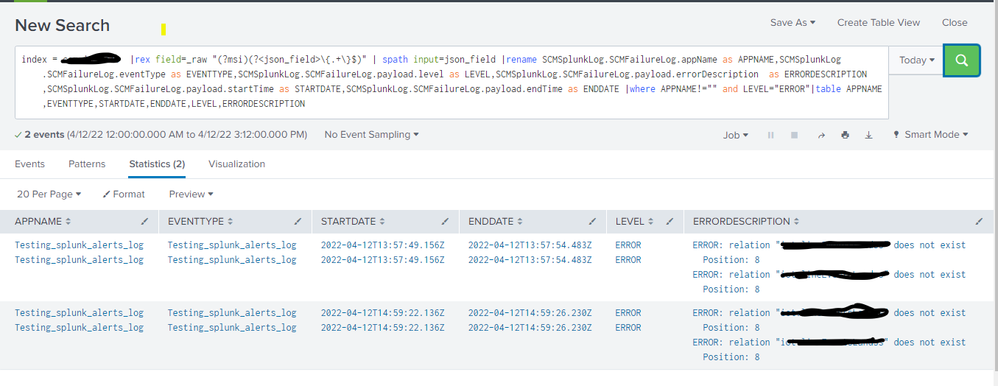
But when i execute the below search query
index = **** |rex field=_raw "(?msi)(?<json_field>\{.+\}$)" | spath input=json_field |rename SCMSplunkLog.SCMFailureLog.appName as APPNAME,SCMSplunkLog.SCMFailureLog.eventType as EVENTTYPE,SCMSplunkLog.SCMFailureLog.payload.level as LEVEL,SCMSplunkLog.SCMFailureLog.payload.errorDescription as ERRORDESCRIPTION,SCMSplunkLog.SCMFailureLog.payload.startTime as STARTDATE,SCMSplunkLog.SCMFailureLog.payload.endTime as ENDDATE |where APPNAME!="" and LEVEL="ERROR"|table APPNAME,EVENTTYPE,STARTDATE,ENDDATE,LEVEL,ERRORDESCRIPTION
I was getting duplicate entries on result table as below
Can anyone please help me with this.
Edited:
Attached sample json:
{
"SCMSplunkLog" : {
"SCMFailureLog" : {
"appName" : "Testing_splunk_alerts_log",
"eventType" : "Testing_splunk_alerts_log",
"payload" : {
"level" : "ERROR",
"startTime" : "2022-04-12T13:57:49.156Z",
"successCount" : 0,
"failureCount" : 0,
"publishedCount" : 0,
"errorCode" : 0,
"errorDescription" : "ERROR: relation \"test.testLand\" does not exist\n Position: 8",
"sourceCount" : 0,
"endTime" : "2022-04-12T13:57:54.483Z"
}
}
}
}
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
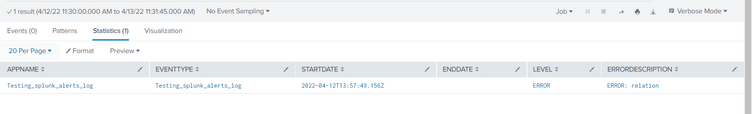
I tried the same that you have. It seems working as expected.
| makeresults | eval _raw="{
\"SCMSplunkLog\" : {
\"SCMFailureLog\" : {
\"appName\" : \"Testing_splunk_alerts_log\",
\"eventType\" : \"Testing_splunk_alerts_log\",
\"payload\" : {
\"level\" : \"ERROR\",
\"startTime\" : \"2022-04-12T13:57:49.156Z\",
\"successCount\" : 0,
\"failureCount\" : 0,
\"publishedCount\" : 0,
\"errorCode\" : 0,
\"errorDescription\" : \"ERROR: relation \"test.testLand\" does not exist\n Position: 8\",
\"sourceCount\" : 0,
\"endTime\" : \"2022-04-12T13:57:54.483Z\"
}
}
}
}"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@mayurr98 updated my post with sample JSON
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you please give us sample JSON raw events. paste in </>