- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why is Extracted field not searchable?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why is Extracted field not searchable?
I have logs that seem to be extracting perfectly. All fields show up in "Interesting Fields", and each one can be searched (myField=*) gives results.
EXCEPT:
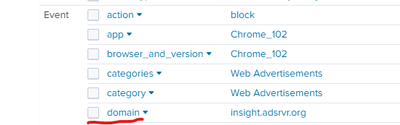
I have a field called "domain". It cannot be searched. It is there. It shows 100% of events have it. I hover over it and i see the contents. But when I run a search, nada.
index=disa-cbii
Search
index=disa-cbii domain="insight.adsrvr.org"
0 Results found.
Same for domain=*
Now, if we throw in spath
index=disa-cbii
| spath domain
| search domain="insight.adsrvr.org"
we get plenty of results.
What is happening? From everything i can tell, I should not need spath because the event is extracting just fine. All the other dozen fields are extracted and searchable.
index=disa-cbii
| table domain
works fine. How can I table something that doesn't exist?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @oliverja,
if you said the using the spath command you see the data, I suppose that you're speaking of json format, did you used the INDEXED_EXTRACTION=JSON in your props.conf?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have "KV_MODE = json" in my props.conf, which I took to mean that my extractions could take place at search time, instead of index time.
If I do your solution, I would need to disable the KV_MODE so that it is not doing the same work twice? But it would be done on the ingest/index side, not search. We get a lot of these, and I am worried about the storage implications.
I also want to add -- "domain" shows up as covering 100% of events. Again implying it is working?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any more clarification before I start overriding things?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @oliverja,
as I said, I usually use INDEXED_EXTRACTIONS = JSON and it always correctly runs but kv_mode = json should still work.
Anyway, if the problem is only on one field (domain) maybe the easiest solution is to add a regex extraction on ly for this field, to avoid to change all your extractions.
Ciao.
giuseppe