- Splunk Answers
- :
- Using Splunk
- :
- Splunk Dev
- :
- Why does Splunk Cloud Custom app request fail for ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why does Splunk Cloud Custom app request fail for the package created locally?
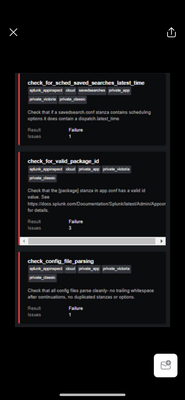
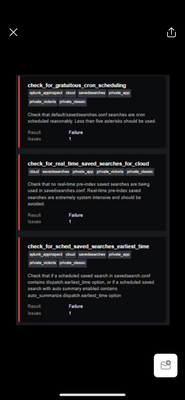
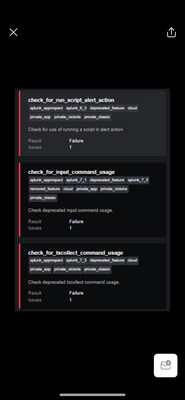
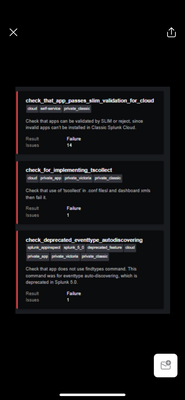
Hi Team, I have been trying to create a custom app with some config files and created it manually with the directory structures. But once submitted, I came across the below failures as mentioned by splunk.
splunk.
please help me how I can solve the issues and also let me know if there are any other ways to package the app if I have some config items
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's a lot of errors...
Start with the Cloud Appinspect Criteria. Hopefully something obvious jumps out.
If that doesn't help then it's going to be very hard to help debug this without some more details about what your app contains. Feel free to share the (obfuscated) config within the app and the high-level structure too.
If you (understandably) don't want to share this on here then I would raise a ticket for Splunk support.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
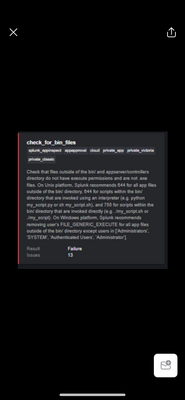
thanks. All the other errors I can sort out except the File_generic_execute issue. Can you assist me to resolve that one?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure no problem.
This validation error pertains to the fact some of your files outside of the bin directory have execute permissions set.
The way to fix this is to remove the execute permissions for any file that does not need to be executed.
WARNING: This command will change file permissions so make sure that you only run this in your app directory (do not run this command elsewhere on your OS), firstly lets find all of the non-bin files in the app because these will not need to have execute permissions.
cd my_app
find -type f -not -path "./bin/*"
Once you're happy that this is finding the correct files, we can then add the permission change:
find -type f -not -path "./bin/*" -exec chmod 644 {} +
Then we'll need to deal with the bin directory, if your bin is entirely Python based, then because Python is an interpreted language (e.g. the Python binary executes and reads the Python scripts) we can remove the execution permissions from the bin contents too:
find -type f -path "./bin/*" -exec chmod 644 {} +
The only thing in your bin that will need execution permissions are shell scripts and other executables. You can explicitly set these individually with a chmod (e.g. allow all users to execute and read my_executable):
chmod 755 ./bin/my_executable