- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- How to fix failure in app-inspect | check_for_supp...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to fix failure in app-inspect | check_for_supported_tls?
Splunk app inspect reports the "check_for_supported_tls" failure with the description as -
If you are using requests.post to talk to your own infra with non-public PKI, make sure you bundle your own CA certs as part of your app and pass the path into requests.post as an arg.
I am using verify: false in the request.post() method and getting the above error in the app inspect tool.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was having the same issue. I was able to fix it by using certifi package to get the location of certificates in the environment and assigning the path to verify.
import certifi
.
.
.
cert_path = certifi.where()
requests.get(url, headers, verify=cert_path)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have the same issue. So, you are saying that from the certifi library, I can extract the path to the SSL certificate bundle and pass it to the post request as an argument, right?
Now, I want to clarify something, the add-on application I have developed needs to be distributed to the clients so, according to this link: https://community.splunk.com/t5/Splunk-Cloud-Platform/How-do-I-go-about-publishing-a-Splunk-Technica... does the client need to put their bundled certificate themselves into the app directory? And use your code to retrieve the path of the cert and pass it as an argument to the post request?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm getting the same issue with my app as well.
I'm just trying to call the Splunk API using requests.get and requests.post, with verify=false.
As the Splunk REST API port 8089 isn't by default ssl-secured, it shouldn't fall to the app developers to make sweeping changes to Splunk's architecture just to call the API.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
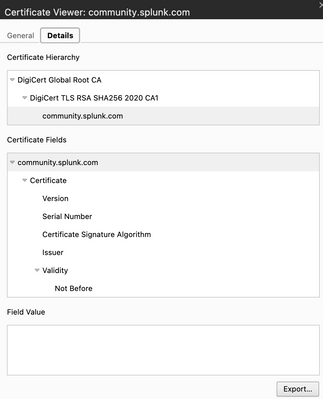
I fixed this issue by generating a bundle certificates file and attaching to my requests, follow these steps:
- on Chrome, click on the padlock icon -> connection is secure -> certificate is valid
- it should show you the certificate, then you have to click on the details tab -> export
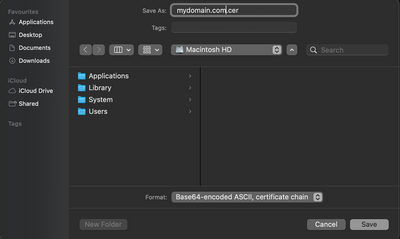
- The most important part is selecting the "Certificate Chain" option when saving, so it will add all the intermediate CA certificates, not only your certificate
- after saved the file, copy it to your repository and point it in the requests like this python snippet:
requests.get(
"myapi.com/whatever/"
verify="/your_repo/mydomain.com.cer"
)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This worked for me, thanks a lot!
Note: the extension of my certificate file was .crt by default. Also, once the certificate expires, you'll have to update this piece of code.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm having the same issue, I guess we will need to copy our server certificates (the one used by nginx or whatever webserver we use) and include within the app and then passing as a parameter in the request?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also getting the same issue with self-install on my Splunk Cloud platform as well. Looking for a solution too