Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Tech Talks
Deep-dives for technical practitioners.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- News & Education
- :
- Practitioner Resources
- :
- Splunk Tech Talks
- :
- Splunk Tech Talks
- :
- Using the Splunk Threat Research Team’s Latest Sec...
Using the Splunk Threat Research Team’s Latest Security Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark Topic
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
WhitneySink

Splunk Employee
02-14-2024
01:53 PM
WATCH NOW
Tech Talk | Security Edition
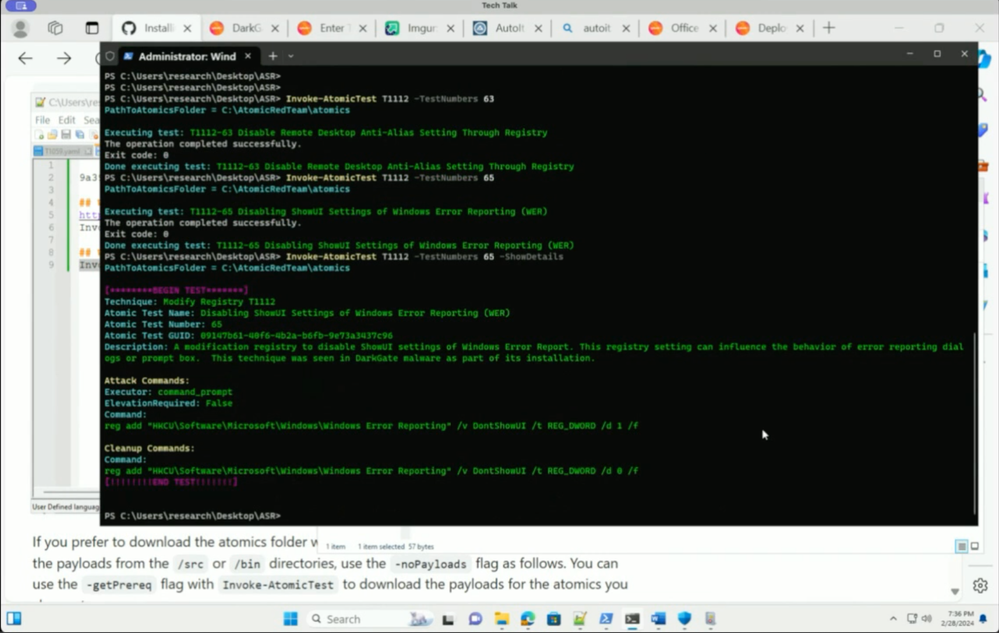
Did you know the Splunk Threat Research Team regularly releases new, pre-packaged security content? Just in the last few months, the team has released dozens of new and updated detections and analytics stories covering the latest threats, including malware campaigns, zero-day vulnerabilities, CVEs, and more.
Join this Tech Talk to learn more from Michael Haag, Principal Threat Researcher, who will provide:
- Best practices for accessing and using the team’s content in the Splunk ES Content Update (ESCU) app
- An overview of the team’s content updates between November and January
- Deeper dives into new content for detecting DarkGate malware, Office 365 account takeover, and Windows Attack Surface Reduction events
WATCH HERE
Labels
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Get Updates on the Splunk Community!
Threat Hunting Unlocked: How to Uplevel Your Threat Hunting With the PEAK Framework ...
WATCH NOWAs AI starts tackling low level alerts, it's more critical than ever to uplevel your threat hunting ...
Splunk APM: New Product Features + Community Office Hours Recap!
Howdy Splunk Community! Over the past few months, we’ve had a lot going on in the world of Splunk Application ...
Index This | Forward, I’m heavy; backward, I’m not. What am I?
April 2024 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with another ...
Labels
-
Admin
1 -
Builder
8 -
DevOps
70 -
Featured
3 -
IT Ops
1 -
Most Valuable Tech Talks
22 -
Observability
57 -
Platform
65 -
Security
99