Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Tech Talks
Deep-dives for technical practitioners.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- News & Education
- :
- Practitioner Resources
- :
- Splunk Tech Talks
- :
- Splunk Tech Talks
- :
- Enhancing Security Operations With Automated Threa...
Enhancing Security Operations With Automated Threat Analysis
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark Topic
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
WhitneySink

Splunk Employee
03-05-2024
02:14 PM
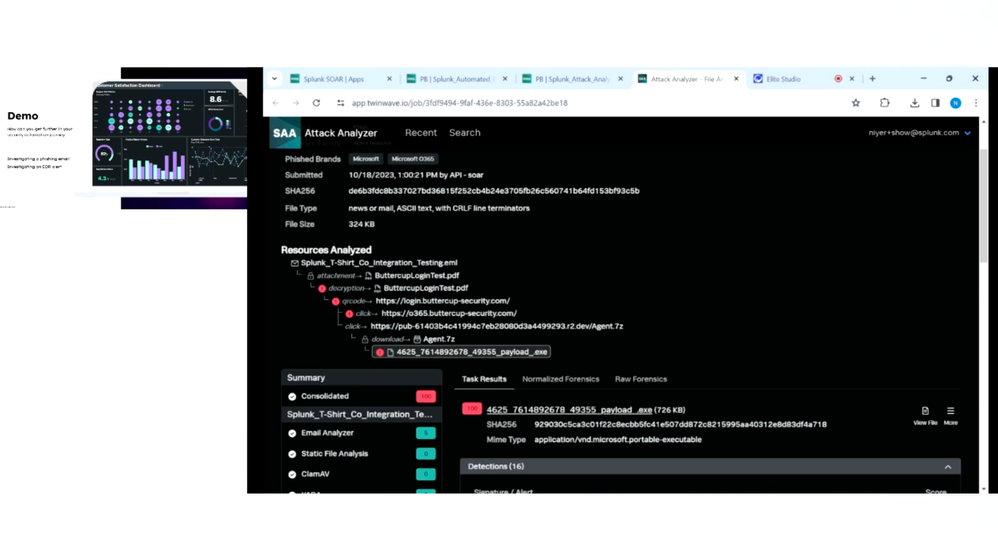
Phishing and malware attacks continue to surge, and phishing campaigns grow increasingly complex – all of which leaves analysts buried under a daily avalanche of alerts.
As threat actors become more adept at evading detection solutions with novel ways to deliver malware, the SOC requires an advanced solution to keep up with the continual shift of threat actor TTPs to protect the enterprise.
Join Sr. Principal Product Manager, Neal Iyer, to learn how automated threat analysis strengthens the overall unified security operations experience of Splunk Security through:
- Initial triage at scale via automated end-to-end threat analysis and response and the ability to prioritize SOAR cases for analyst review
- Enhanced Splunk Enterprise Security (ES) notables with automated analysis of URLs
- Out of the box dashboards that empower SOC leadership to understand patterns in alert volumes and provide blue teams insights on how adversaries are getting past their defenses
Labels
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Get Updates on the Splunk Community!
Index This | I’m short for "configuration file.” What am I?
May 2024 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with a Special ...
New Articles from Academic Learning Partners, Help Expand Lantern’s Use Case Library, ...
Splunk Lantern is a Splunk customer success center that provides advice from Splunk experts on valuable data ...
Your Guide to SPL2 at .conf24!
So, you’re headed to .conf24? You’re in for a good time. Las Vegas weather is just *chef’s kiss* beautiful in ...
Labels
-
Admin
1 -
Builder
8 -
DevOps
70 -
Featured
2 -
IT Ops
1 -
Most Valuable Tech Talks
22 -
Observability
59 -
Platform
65 -
Security
100