Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- replace string (using map/object)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
replace string (using map/object)
hello,
is there anyway to define a map / object. IE { '123': 'something', '1234', 'anotherThing' } and then replace strings with '123' with 'something' and strings with '1234' with 'anotherThing'?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can do that easily using rex mode=sed. but if you have very large number of replacements then rex would not be a right fit.
using rex if you have small number of replacements:
| makeresults
| eval image_name="123_456_789_10"
| rex mode=sed "s/123/something/g" field=image_name
| rex mode=sed "s/456/something2/g" field=image_name
| rex mode=sed "s/789/something3/g" field=image_name
| rex mode=sed "s/10/something5/g" field=image_nameusing kv-store lookup if you have very large number of replacements:
- you need to define kv-store lookup
- you need to have two fields let's call it: number and text
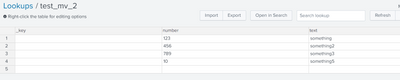
- The kv-store lookup should look like below:
- The final search looks like below:
| makeresults
| eval image_name="123_456_789_10"
| makemv image_name delim="_"
| lookup test_mv_final number as image_name OUTPUT text as decode_image_name
| eventstats list(decode_image_name) as decode_image_name delim="_"
| mvcombine decode_image_nameReason for using kv-store lookup rather csv lookup is to perform lookup against multi value field. lookups are not aware of multivalue fields.
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@thambisetty thanks for the response. let me clarify the question.
i have a field called image_name which is a string. the string is like '123_456_789_10'. and i want to decode the string from an object. like this {123: 'something', 456: 'something2', 789: 'something3', 10: 'something5'}
and i wand to replace the values of the image_name field with the values of the object so the string will be like: something_something2_something3_something5.
hopefully this makes it clearer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
your question is not quite clear.
may be you find below is helpful.
|makeresults
| eval object="{ '123': 'something', '1234', 'anotherThing' }"
| rex mode=sed "s/'123'/'something'/g" field=object
| rex mode=sed "s/'1234'/'anotherThing'/g" field=objectIf this helps, give a like below.