Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: regex extraction
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please try this?
YOUR_SEARCH| rex field=_raw "[0-9]{1,2}:[0-9]{1,2}:[0-9]{1,3}.[0-9]{1,3}\s(?<user>\w+)\s(?<appname>\w+).*signal\:\s(?<signal>.*)"
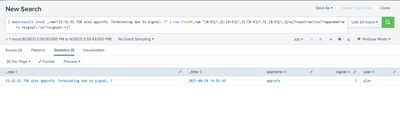
My Sample Search :
| makeresults |eval _raw="23:52:52.758 alex appinfo: Terminating due to signal: 1" | rex field=_raw "[0-9]{1,2}:[0-9]{1,2}:[0-9]{1,3}.[0-9]{1,3}\s(?<user>\w+)\s(?<appname>\w+).*signal\:\s(?<signal>.*)"
Thanks
KV
▄︻̷̿┻̿═━一
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| rex "\S+\s(?<user>\S+)\s(?<appname>\S+):\s.*?signal:\s(?<signal>\d+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please try this?
YOUR_SEARCH| rex field=_raw "[0-9]{1,2}:[0-9]{1,2}:[0-9]{1,3}.[0-9]{1,3}\s(?<user>\w+)\s(?<appname>\w+).*signal\:\s(?<signal>.*)"
My Sample Search :
| makeresults |eval _raw="23:52:52.758 alex appinfo: Terminating due to signal: 1" | rex field=_raw "[0-9]{1,2}:[0-9]{1,2}:[0-9]{1,3}.[0-9]{1,3}\s(?<user>\w+)\s(?<appname>\w+).*signal\:\s(?<signal>.*)"
Thanks
KV
▄︻̷̿┻̿═━一
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it work separately but not work all in same time
Worked
rex field=_raw "[0-9]{1,2}:[0-9]{1,2}:[0-9]{1,3}.[0-9]{1,3}\s(?<user>\w+)
rex field=_raw "[0-9]{1,2}:[0-9]{1,2}:[0-9]{1,3}.[0-9]{1,3}\s(?<appname>\w+)
rex field=_raw "[0-9]{1,2}:[0-9]{1,2}:[0-9]{1,3}.[0-9]{1,3} .*signal\:\s(?<signal>.*)"
Not worked
| rex field=_raw "[0-9]{1,2}:[0-9]{1,2}:[0-9]{1,3}.[0-9]{1,3}\s(?<user>\w+)\s(?<appname>\w+).*signal\:\s(?<signal>.*)"
any idea?
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's working for me on your given sample data. Can you please share those sample events which are not extracting?