Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: issue querying events in quotes
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seeing issue with tabling results inside quotes and wondering if this is know issue with work around?
query:
index=perfmon source=process sourcetype=WinHostMon ProcessId=22864
results:
Type=Process
Name="splunkd.exe"
ProcessId=22864
CommandLine=""C:\Program Files\SplunkUniversalForwarder\bin\splunkd.exe" service"
StartTime="20160817005341.861352+120"
Host="myhost"
Path="C:\Program Files\SplunkUniversalForwarder\bin\splunkd.exe"
Type=Process
Name="TrustedInstaller.exe"
ProcessId=19228
CommandLine="C:\Windows\servicing\TrustedInstaller.exe"
StartTime="20160816000024.970946+120"
Host="Anotherhost"
Path="C:\Windows\servicing\TrustedInstaller.exe"
query:
index=perfmon source=process sourcetype=WinHostMon ProcessId=22864 | table CommandLine
No results..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, the double quotes give little trouble there..
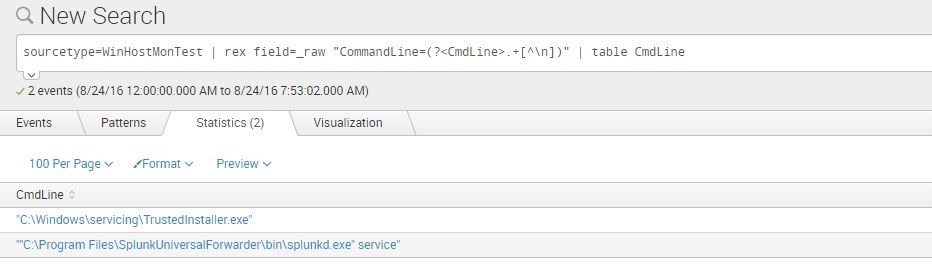
maybe, a quick rex.. tested this and works fine..
sourcetype=WinHostMonTest | rex field=_raw "CommandLine=(?<CmdLine>.+[^\n])" | table CmdLine
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, the double quotes give little trouble there..
maybe, a quick rex.. tested this and works fine..
sourcetype=WinHostMonTest | rex field=_raw "CommandLine=(?<CmdLine>.+[^\n])" | table CmdLine
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Legend!
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there any way to have this data straightened out with a props/transform search time or index time extraction?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I cant seem to put this in my dashboard:
...| rex field=_raw "CommandLine=(?.+[^\n])"| table CommandLine
Its complaining about the
<title>$ProcessID$ Process Drilldown</title>
<search>
<query>index=perfmon source=process sourcetype=WinHostMon ProcessId=22864
earliest=$time.earliest$ latest=$time.latest$ host=$Host$ ProcessId=$ProcessID$ | dedup ProcessId | rex field=_raw "CommandLine=(?.+[^\n])"| table Name ProcessId CommandLine Path
true
true
none
none
10
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i am not sure of this one.. let me create a dashboard to check it and update you back..
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CDATA! sorted it. Thanks