Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: ipmask (dys-)function
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ipmask (dys-)function: Why the SPL parser does not handle this fairly common case?
The documentation (9.0.2 Search Reference) describes a function ipmask(<mask>,<ip>) that is supposed to apply the given netmask to the given IP. Seems pretty simple, and the examples are mostly straightforward... unless you consider what a netmask of 0.255.0.244 would actually mean on the network.
The more interesting problem is what you're allowed to pass to this function. From what I can tell, the first parameter MUST be a quoted string of digits, and particularly NOT the name of a field in your data:
|makeresults 1 | eval ip = "1.2.3.4", mask = "255.255.255.0"
With these values defined,
| eval k = ipmask("255.255.255.0", "5.6.7.8") works fine, k=5.6.7.0
| eval k = ipmask("255.255.255.0", ip) works fine, k=1.2.3.0
| eval k = ipmask("255.255.255.0", mask) works fine, k=255.255.255.0 (but isn't a meaningful calculation).
| eval k = ipmask(mask, "5.6.7.8") does not work: Error in 'EvalCommand': The arguments to the 'ipmask' function are invalid.
| eval k = ipmask(mask, ip) does not work: Error in 'EvalCommand': The arguments to the 'ipmask' function are invalid.
I'm sure there's some highly technical reason why the SPL parser does not handle this fairly common case, and if there's anyone who can share that reason, I'd love to hear it.
--Joe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
The inability to pass a field name as the first argument of ipmask prevents this function from calculating the network address when the netmask is variable.
Also, with IPv6 addresses, it cannot be used as a method of calculating network addresses.
This seems to limit the use of the ipmask function very much.
I added the following external command lookup to the App below as an alternative method of ipmask.
Usage:
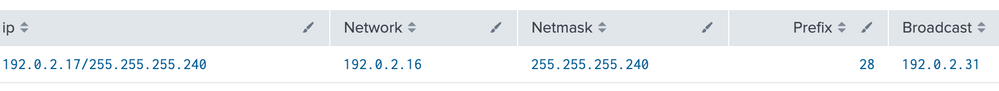
| makeresults
| eval ip="192.0.2.17/255.255.255.240"
| lookup local=t ipcalclookup Address as ip OUTPUT Network Netmask Prefix Broadcast
| table ip Network Netmask Prefix Broadcast
Input Address can also be in the following format.
* ip/netmask: e.g. 192.0.2.17/255.255.255.240
* ip/prefix: e.g. 192.0.2.17/28
* ipv6/prefix: e.g. 2001:db8:1234::1/64
Numeral system macros for Splunk
https://splunkbase.splunk.com/app/6595
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Time to hit Ideas🤣