Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- include date in request - stats count
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
include date in request - stats count
numeroinconnu12
Path Finder
11-21-2019
10:08 AM
Hello,
I have a problem.
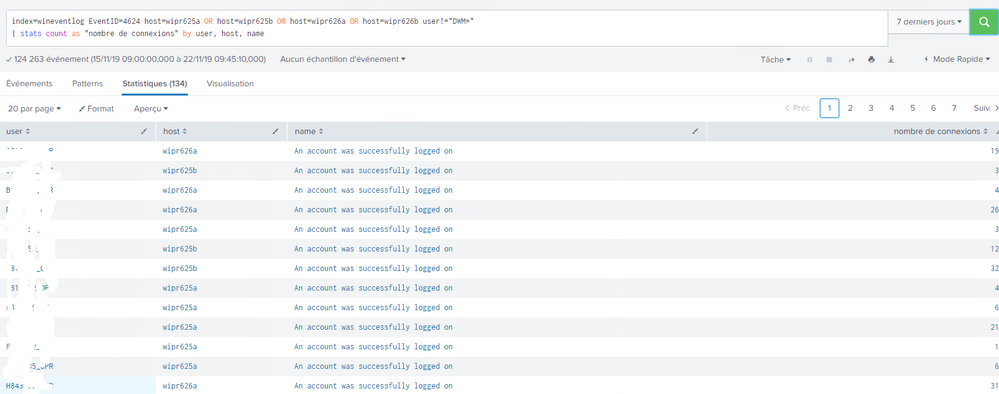
This is my request, it works well.
index=wineventlog EventID=4624 host=wipr625a OR host=wipr625b OR host=wipr626a OR host=wipr626b user!="DWM*"
| stats count as "nombre de connexions" by user, host, name
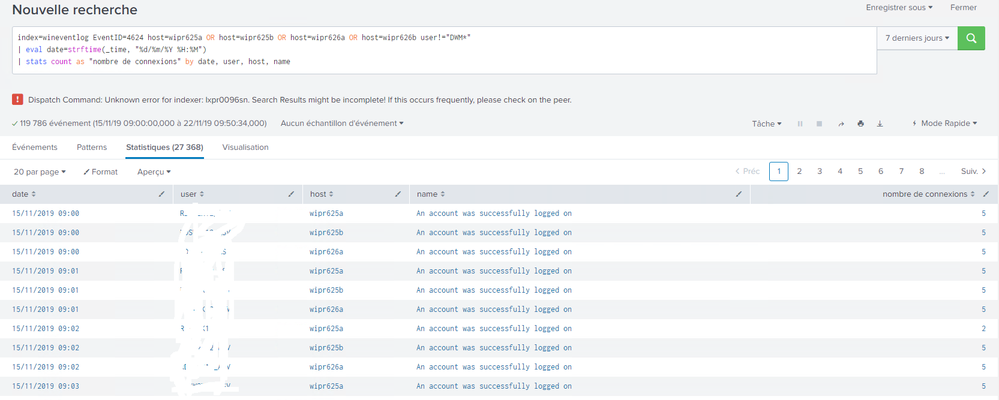
I would like to include the date in my results and that's how I modified my request, only with that request my results are wrong, did I forget something?
index=wineventlog EventID=4624 host=wipr625a OR host=wipr625b OR host=wipr626a OR host=wipr626b user!="DWM*"
| eval date=strftime(_time, "%d/%m/%Y %H:%M")
| stats count as "nombre de connexions" by user, date, host, name
thanks !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HiroshiSatoh
Champion
11-21-2019
09:20 PM
The search statement is correct. Please tell us specifically about the problem.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HiroshiSatoh
Champion
11-22-2019
01:24 AM
Is the problem that the number of results is different?
Did you check the displayed error?
https://answers.splunk.com/answers/506621/unknown-error-for-peer-xxx-search-results-might-be.html
How about the following search statement?
| bin span=1m _time
| stats count as "nombre de connexions" by user, _time, host, name
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
numeroinconnu12
Path Finder
11-22-2019
12:54 AM
Get Updates on the Splunk Community!
Application management with Targeted Application Install for Victoria Experience
Experience a new era of flexibility in managing your Splunk Cloud Platform apps! With Targeted Application ...
Index This | What goes up and never comes down?
January 2026 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Splunkers, Pack Your Bags: Why Cisco Live EMEA is Your Next Big Destination
The Power of Two: Splunk + Cisco at "Ludicrous Scale"
You know Splunk. You know Cisco. But have you seen ...