Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: how to count records in a row?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello guys, I am new with a splunk and i need some help (also a splunk search language documentation with example).
My search row is
index=waf source="waf_events" | stats count by remote_addr, msg | mvcombine msg
As a result I have a row:
IP address rule name count
192.168.1.1 Anomally connection 1
Bad user name
It show IP address and rules name, that IP address broke rules and a count of IP address, But i want, that it will show a rule count. Something like this:
192.168.1.1 Anomally connection, Bad user name 2 (two rules)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Pikta,
about Splunk Search documentation, you can see at https://docs.splunk.com/Documentation/Splunk/8.1.3/SearchTutorial/WelcometotheSearchTutorial and https://www.splunk.com/en_us/training/free-courses/splunk-fundamentals-1.html
About your need, you can add the dc (distinct count) option to have the number of rules, something like this:
index=waf source="waf_events"
| stats values(rule_names) AS rulenames dc(rule_names) AS dc_rulenames by remote_addrFor more infos see at https://docs.splunk.com/Documentation/Splunk/8.1.3/SearchReference/Stats or https://www.tutorialspoint.com/splunk/splunk_stats_command.htm#:~:text=The%20stats%20command%20is%20....
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Pikta,
about Splunk Search documentation, you can see at https://docs.splunk.com/Documentation/Splunk/8.1.3/SearchTutorial/WelcometotheSearchTutorial and https://www.splunk.com/en_us/training/free-courses/splunk-fundamentals-1.html
About your need, you can add the dc (distinct count) option to have the number of rules, something like this:
index=waf source="waf_events"
| stats values(rule_names) AS rulenames dc(rule_names) AS dc_rulenames by remote_addrFor more infos see at https://docs.splunk.com/Documentation/Splunk/8.1.3/SearchReference/Stats or https://www.tutorialspoint.com/splunk/splunk_stats_command.htm#:~:text=The%20stats%20command%20is%20....
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, @gcusello , Thank for a solution. Another question:
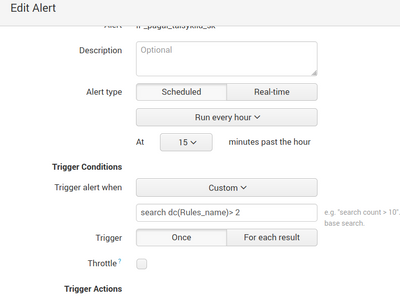
Now I want to create a custom alert, that a splunk will send me an email when a rule count is more than 3. I tried to write in "Trigger alert when" many variations, but no one works. The last one was "search dc(rule_names) > 2" But I am getting an email event then when dc(rule_name)=1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Pikta,
this is another question and, next time, please, open a new question.
Anyway, you have to put the threeshold in the search, something like this:
index=waf source="waf_events"
| stats values(rule_names) AS rulenames dc(rule_names) AS dc_rulenames by remote_addr
| where dc_rulenames>3Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had this one , when I wrote, that I want to get an alert to my email, when rules count is more than 3.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Pikta,
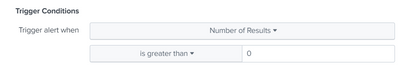
if you use the threeshold in the search, the condition to put in the alert is "Number of Results is greather than 0".
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks one more time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Pikta,
good for you, see next time.
Ciao and happy splunking.
Giuseppe
P.S.: Karma Points are appreciated 😉