Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- help me in writing Regex for the below data
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
<37>Aug 27 10:52:59 DC1TPSMS02 CEF:0|TippingPoint|UnityOne|1.0.0.17|7611|Suspicious Country Blacklist|1|app=IP cnt=1 dst=192.54.112.30 dpt=53 act=Block cn1=0 cn1Label=VLAN ID cn2=33554431 cn2Label=Taxonomy cn3=0
from above data i want to extract below line
Aug 27 10:52:59 DC1TPSMS02 CEF:0|TippingPoint
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @vikram1583
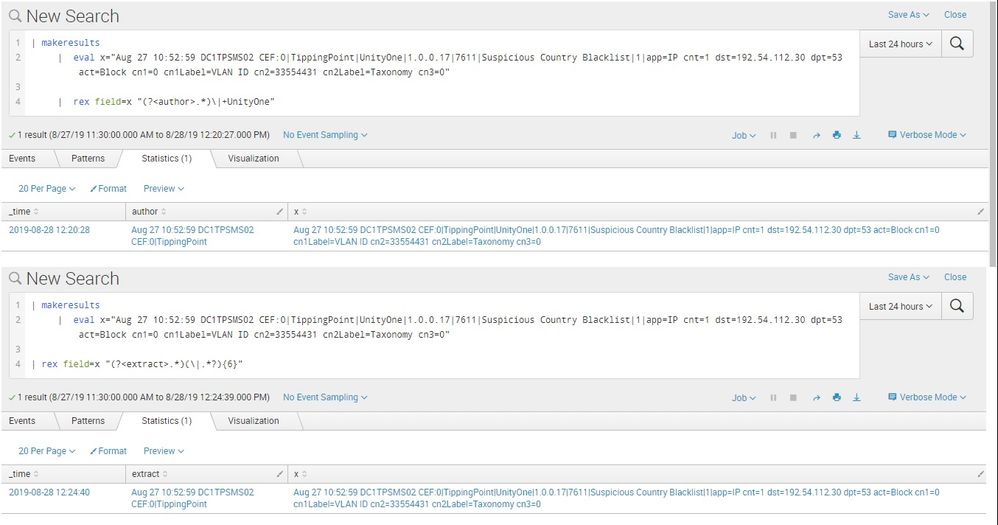
Please see below screen shot from my and @jpolvino 's rexes, see the author field in first query and extract field in the second query.
Where are you checking for the these fields after you run your rex?Please hardcode first n confirm that the author or extract filed output is what you need
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Data coming from cloud through heavy forwarder
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes this is working can you send me props to validate this data before coming to indexer I want that line to come as an event
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @vikram1583
Please see below screen shot from my and @jpolvino 's rexes, see the author field in first query and extract field in the second query.
Where are you checking for the these fields after you run your rex?Please hardcode first n confirm that the author or extract filed output is what you need
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Assuming it is always in the same position, this may work for you:
(your search)
| rex "(?<extract>.*)(\|.*?){6}"
Or
(your search)
| rex "(?<extract>(([^|]+)\|)\w+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is also not working
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then we need more detail please. You have 2 responses with confirmed working results. Is your event in a field, or is it _raw?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jpolvino your rex is getting corrupted while pasting as a comment, it works for the answer you gave though, I think vikram has copied rex from your comments as it is and is getting rex errors
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I see corrupted values. @vikram1583 please type a solution in manually.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @vikram1583
your initial query is index=email (host=10.114.5. OR host=10.124.5.) NOT default tippingpoint | rex whatever...
Remove the rex and first see whether you are receiving the event on which you want to apply rex. 2 possible issue - the earliest time range is excluding those events and I am also not ok with the NOT condition, if you mean to exclude default tippongpoint use it like this
index=email (host=10.114.5. OR host=10.124.5.) NOT ("default tippingpoint")
You might get nothing returned but you will not get a splunk syntax error on using the rexes, so when you say not working - what is not wokring?
@jpolvino - I think we need to ensure first that the source event is properly captured, rex is working but failing because of that. It is very late at night here, i will look into this again tomorrow in case this is still an issue
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jpolvino | rex "(?.)(|.?){6}" while i am using this rex i am not getting any error, it is not changing anything in the event it remains the same
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Sukisen1981 same thing with your rex i am not getting any error but results did not change same event is coming
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
not working
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Odd, they work for me. Is the event you posted accurate, even the pipe characters? Borrowing SPL from Sukisen1981:
| makeresults
| eval x="Aug 27 10:52:59 DC1TPSMS02 CEF:0|TippingPoint|UnityOne|1.0.0.17|7611|Suspicious Country Blacklist|1|app=IP cnt=1 dst=192.54.112.30 dpt=53 act=Block cn1=0 cn1Label=VLAN ID cn2=33554431 cn2Label=Taxonomy cn3=0"
| rex field=x "(?.)(|.?){6}"
| table extract
Produces:
Aug 27 10:52:59 DC1TPSMS02 CEF:0|TippingPoint
So does the other example. I'm curious what you get!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
<37>Aug 27 11:57:42 DC1TPSMS02 CEF:0|TippingPoint|UnityOne|1.0.0.17|7610|Blacklist|1|app=IP cnt=1 dst=208.87.176.250 dpt=389 act=Block cn1=613 cn1Label=VLAN ID cn2=33554431 cn2Label=Taxonomy cn3=0 cn3Label=Packet Trace cs1=CDE Perimeter Outbound cs1Label=Profile Name cs2=b005e16a-02dd-493c-a525-ba7c10c3e66c cs2Label=Policy UUID cs3=00000001-0001-0001-0001-000000007610 cs3Label=Signature UUID cs4=1 cs4Label=DeviceSegment cs5= cs5Label=SMS Name dvchost=DC1-IPS-04 cs6=185.94.111.1 cs6Label=Filter Message Parms srcip=185.94.111.1 spt=45138 externalId=115756483 rt=1566932262858 cat=Reputation proto=IP deviceInboundInterface=26 c6a2= c6a2Label=Source IPv6 c6a3= c6a3Label=Destination IPv6 request= requestMethod= dhost= sourceTranslatedAddress=185.94.111.1 c6a1= c6a1Label=Client IPv6 suser= sntdom= duser= dntdom=
host = 10.114.5.250 source = tcp:514 sourcetype = cisco:esa:legacy
This is the actual event
My search: index=email earliest=-10m (host=10.114.5.* OR host=10.124.5.*) NOT default tippingpoint | rex "(?(([^|]+)|)\w+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
<37>Aug 27 12:04:17 DC1TPSMS02 CEF:0|TippingPoint|UnityOne|1.0.0.17|7610|Blacklist|1|app=IP cnt=1 dst=208.87.176.47 dpt=8089 act=Block cn1=613 cn1Label=VLAN ID cn2=33554431 cn2Label=Taxonomy cn3=0 cn3Label=Packet Trace cs1=CDE Perimeter Outbound cs1Label=Profile Name cs2=b005e16a-02dd-493c-a525-ba7c10c3e66c cs2Label=Policy UUID cs3=00000001-0001-0001-0001-000000007610 cs3Label=Signature UUID cs4=1 cs4Label=DeviceSegment cs5= cs5Label=SMS Name dvchost=DC1-IPS-04 cs6=185.216.140.16 cs6Label=Filter Message Parms srcip=185.216.140.16 spt=52075 externalId=115757480 rt=1566932657158 cat=Reputation proto=IP deviceInboundInterface=26 c6a2= c6a2Label=Source IPv6 c6a3= c6a3Label=Destination IPv6 request= requestMethod= dhost= sourceTranslatedAddress=185.216.140.16 c6a1= c6a1Label=Client IPv6 suser= sntdom= duser= dntdom=
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try putting this in your rex double quotes:
(?.)(|.?){6}
Do you get a Splunk error?
Try formatting your search like this:
index=email (host=10.114.5. OR host=10.124.5.) NOT default tippingpoint earliest=-10m | rex "(?.)(|.?){6}"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=email (host=10.114.5. OR host=10.124.5.) NOT default tippingpoint earliest=-10m | rex "(?.)(|.?){6}"
I am getting this error
Error in 'rex' command: Encountered the following error while compiling the regex '(?.)(|.?){6}': Regex: unrecognized character after (? or (?-.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| rex field=_raw "(?<author>.*)\|+UnityOne"
or
| makeresults
| eval x="Aug 27 10:52:59 DC1TPSMS02 CEF:0|TippingPoint|UnityOne|1.0.0.17|7611|Suspicious Country Blacklist|1|app=IP cnt=1 dst=192.54.112.30 dpt=53 act=Block cn1=0 cn1Label=VLAN ID cn2=33554431 cn2Label=Taxonomy cn3=0"
| rex field=x "(?<author>.*)\|+UnityOne"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| rex field=x "(?.*)|+UnityOne" This Rex is working
i want to validate it before coming to the indexer want to write props for this can you please send me props Please
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not working