- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- exclude certain event type from count
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I have a stat on eventtype like this
index=xyz | stats count by eventtype
This query generates:
All_logs = 14
Error = 2
Login = 4
Auth = 8
Where All_logs is also an eventtype which encomapsses all events: Error, Login and Auth
How can I rewrite this query so I will see count of eventtype excluding All_logs and Login events
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=xyz | stats count by eventtype | search eventtype IN (“Error”,”Auth”)
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I used many dummy fields to make you understand
| makeresults | eval _raw="eventtype,
All_logs,
Error|All_logs,
Login|All_logs,
Auth|All_logs"
| multikv forceheader=1 `comment("prepares sample dataset")`
| makemv eventtype delim="|"
| eval eventtype_dup=eventtype
| mvcombine eventtype_dup delim=","
| rex field=eventtype_dup mode=sed "s/All_logs//g"
| fillnull eventtype_dup
| eval eventtype_dup2=if(eventtype_dup=="",eventtype,eventtype_dup)
| stats count by eventtype_dup2
up vote if it solves your issue.
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@thambisetty , still seeing All_logs and Login events in the stats count 😞
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
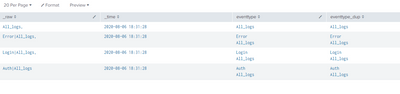
if you looked at my answer, it contains 4 rows like below
Look at eventtype field All_logs is present in all rows but if you see final output the count of All_logs below is 1 because All_logs is present in one row alone with out any other value.
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@thambisetty , I am sorry, my post probably was not very clear. Let me rephrase...
Original query: index=xyz | stats count by eventtype
where All_logs encompasses every log in the search (100% coverage).
Current Result:
eventtype | count |
All_logs | 14 |
Error | 2 |
Login | 4 |
Auth | 8 |
Expected Result:
eventtype | count |
Error | 2 |
Auth | 8 |
Appreciate all your help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=xyz | stats count by eventtype | search eventtype IN (“Error”,”Auth”)
If this helps, give a like below.