Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- creating a correlation search for data exfiltratio...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
creating a correlation search for data exfiltration via email using datamodel
Hi all,
I am trying to create a correlation search query for "data exfiltration via email" using email datamodel
the rule description is: "Sending of multiple emails from a single user(outgoing email from a company employee) with total size exceeding threshold of 100MB within 30 minutes"
my current correlation search is
tstats summariesonly=true sum(All_Email.file_size) as file_size, dc(All_Email.recipient_count) as recipient_count FROM datamodel=Email.All_Email WHERE NOT All_Email.src_category="servers" BY "All_Email.src_user" _time
| `drop_dm_object_name("All_Email")`
| rex field=email "@(?<domain>.*)"
| eval direction=if(in(domain, "xxx.com.au", "yyy.com.au", "aaa.com.au"), "outbound", "inbound")
| eval file_size=round(file_size/(100000000))
| where file_size>100
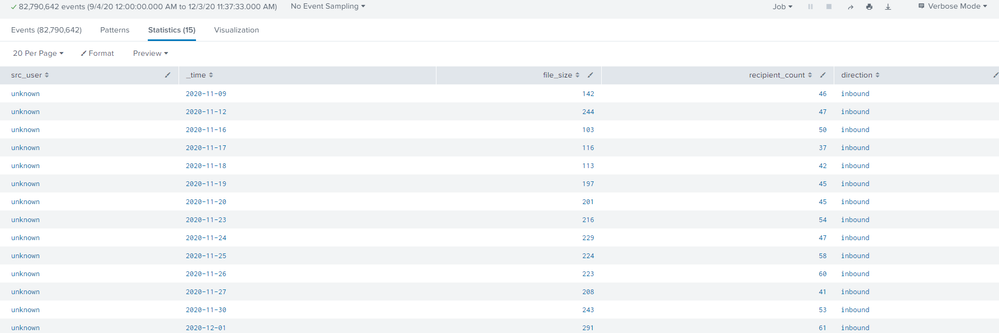
and part of the result is
as you can see the src_user values show "unknown" and I only see the inbound emails.
Please share your opinion which you think it could enhance the correlation search.
Thanks