Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- count number of arguments in bat file
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
count number of arguments in bat file
I'm trying to count of the number of occurrences / frequency /variations of arguments appearing for a bat file. For example, GradeReport.bat has this template:
GradeReport.bat "grade criteria" "start date" "end date" course# CSV_format
Example:
1) GradeReport.bat "Best grade" "07/20/2021" "07/27/2021" 135629 CSV
2) GradeReport.bat "Average grade" "" "07/27/2021" "" CSV
3) GradeReport.bat "Best grade" "" "" 225386 CSV
4) GradeReport.bat "Student grade" "07/16/2021" "" "" CSV
The query would return:
First argument count: 4
Second argument count: 2
Third argument count: 2
"Best grade" = 2
"Average grade" = 1
"Student grade" = 1
etc.
Thanks for the help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The part before the blank lines just sets up some example data as you showed - the part after the blank lines extracts the fields and counts the occurrences.
| makeresults
| eval _raw="GradeReport.bat \"Best grade\" \"07/20/2021\" \"07/27/2021\" 135629 CSV
GradeReport.bat \"Average grade\" \"\" \"07/27/2021\" \"\" CSV
GradeReport.bat \"Best grade\" \"\" \"\" 225386 CSV
GradeReport.bat \"Student grade\" \"07/16/2021\" \"\" \"\" CSV"
| multikv noheader=t
| fields _raw
| fields - _time
| rex "(?<batfile>\S+)\s+\"(?<grade>[^\"]+)\"\s+\"(?<start>[^\"]*)\"\s+\"(?<end>[^\"]*)\"\s\"?(?<number>\d*)\"?\s+(?<format>.*)"
| foreach *
[| eval <<FIELD>>=if(<<FIELD>>="",null(),<<FIELD>>)]
| stats count(grade) as first_count count(start) as second_count count(end) as third_count count(number) as fourth_count count as grade_count by grade
| eval {grade}=grade_count
| fields - grade grade_count
| stats sum(*) as *- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello!
So I don't know of a way to get all of those in one search. It is very doable in a couple searches though!
You should be able to do
index=main
| stats count by "Grade Criteria"and get the count per result in each field.
As for your ask for an argument count, that's pretty tricky actually! There may be more elegant ways of doing that, but I settled on the following (I've named the fields generically)
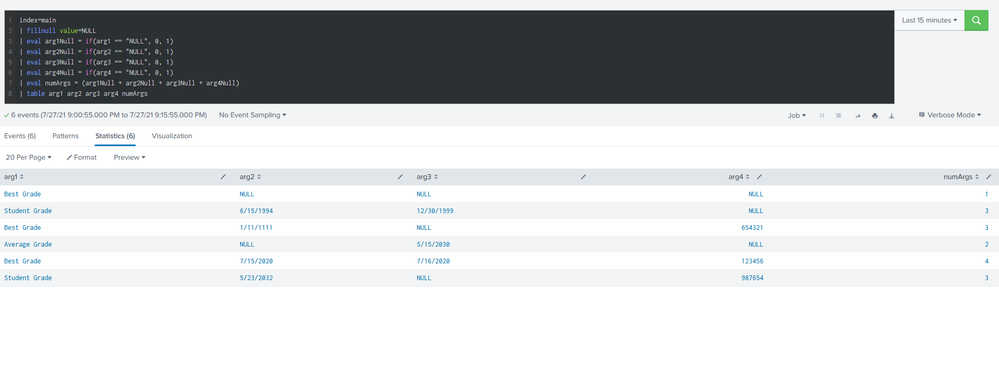
index=main
| fillnull value=NULL
| eval arg1Null = if(arg1 == "NULL", 0, 1)
| eval arg2Null = if(arg2 == "NULL", 0, 1)
| eval arg3Null = if(arg3 == "NULL", 0, 1)
| eval arg4Null = if(arg4 == "NULL", 0, 1)
| eval numArgs = (arg1Null + arg2Null + arg3Null + arg4Null)
| table arg1 arg2 arg3 arg4 numArgsThat is going to take all of your null values, or fields without a value in them, and fill them with the string "NULL". We then create fields checking whether or not the original field was NULL. i.e. if arg1 has a value, it arg1Null gets a value of 1. If it was filled with "NULL", it gets a 0.
We do this for each field, then create a field called numArgs which adds all of them up.
I am not sure if that is the most elegant way of doing things, but I was able to get that working!
Its easy enough to rename the fields from arg1 to "Best Grade" and so on to work with your data.