- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- combine result foreach
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
I have a auditd search like type=EXECVE msg=audit(16): a0="sendmail" a1="-t"
I would like one field with any field like a (a0, a1, a2, a3 ect..)
I try:
"type=EXECVE msg=audit(16): argc=2 a0="sendmail""
| foreach a* [ eval test = test + '<<FIELD>>' ]
No result, I need you help please.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| foreach a*
[| eval test=if(isnull(test),'<<FIELD>>',if(isnull(<<FIELD>>),test,test + " " + '<<FIELD>>')) ]- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
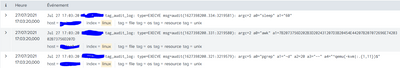
You can try ton import this log to test
Jul 27 17:40:22 myserver tag_audit_log: type=EXECVE msg=audit(1627400420.972:3224562): argc=2 a0="sleep" a1="60"
Jul 27 17:40:22 myserver tag_audit_log: type=EXECVE msg=audit(1627400420.969:3224561): argc=2 a0="awk" a1=7B2073756D202B3D202431207D3B20454E44207B207072696E7420302B73756D207D
Jul 27 17:40:22 myserver tag_audit_log: type=EXECVE msg=audit(1627400420.959:3224560): argc=5 a0="pgrep" a1="-d" a2=20 a3="--" a4="^qemu(-kvm|:.{1,11})$"
Jul 27 17:40:22 myserver tag_audit_log: type=EXECVE msg=audit(1627400420.957:3224559): argc=3 a0="awk" a1=2F5E284D656D467265657C427566666572737C436163686564293A2F207B66726565202B3D2024327D3B20454E44207B7072696E7420667265657D a2="/proc/meminfo"
Jul 27 17:40:14 myserver2 tag_audit_log: type=EXECVE msg=audit(1627400406.970:4065704): argc=2 a0="rm" a1=2F6170706C692F687270726F642F66696C652F50415046472F5053424B335754322E43A35051
Jul 27 17:40:14 myserver2 tag_audit_log: type=EXECVE msg=audit(1627400406.969:4065703): argc=2 a0="rm" a1=2F6170706C692F687270726F642F66696C652F50415046472F5053424B3357592E43A35051
Jul 27 17:40:14 myserver2 tag_audit_log: type=EXECVE msg=audit(1627400406.969:4065702): argc=2 a0="rm" a1=2F6170706C692F687270726F642F66696C652F50415046472F50534244494E54572E43A35051
Jul 27 17:40:14 myserver2 tag_audit_log: type=EXECVE msg=audit(1627400406.968:4065701): argc=2 a0="rm" a1=2F6170706C692F687270726F642F66696C652F50415046472F5053424B3357582E43A35051
Jul 27 17:40:04 myserver2 tag_audit_log: type=EXECVE msg=audit(1627400401.903:4065686): argc=2 a0="date" a1="+%Y%m"
Jul 27 17:40:04 myserver2 tag_audit_log: type=EXECVE msg=audit(1627400401.900:4065685): argc=2 a0="date" a1="+%d"
Jul 27 17:40:04 myserver2 tag_audit_log: type=EXECVE msg=audit(1627400401.898:4065684): argc=4 a0="/bin/sh" a1="/usr/lib64/sa/sa1" a2="1" a3="1"
Jul 27 17:40:04 myserver2 tag_audit_log: type=EXECVE msg=audit(1627400401.897:4065683): argc=3 a0="/bin/sh" a1="-c" a2=2F7573722F6C696236342F73612F73613120312031
Jul 27 17:40:02 myserver tag_audit_log: type=EXECVE msg=audit(1627400401.428:3224556): argc=8 a0="/usr/lib64/sa/sadc" a1="-F" a2="-L" a3="-S" a4="DISK" a5="1" a6="1" a7="-"
Jul 27 17:40:02 myserver tag_audit_log: type=EXECVE msg=audit(1627400401.427:3224555): argc=2 a0="date" a1="+%Y%m"
Jul 27 17:40:02 myserver tag_audit_log: type=EXECVE msg=audit(1627400401.426:3224554): argc=2 a0="date" a1="+%d"
Jul 27 17:40:02 myserver tag_audit_log: type=EXECVE msg=audit(1627400401.424:3224553): argc=4 a0="/bin/sh" a1="/usr/lib64/sa/sa1" a2="1" a3="1"
Jul 27 17:40:02 myserver tag_audit_log: type=EXECVE msg=audit(1627400401.423:3224552): argc=3 a0="/bin/sh" a1="-c" a2=2F7573722F6C696236342F73612F73613120312031
Jul 27 17:39:22 myserver tag_audit_log: type=EXECVE msg=audit(1627400360.956:3224546): argc=2 a0="sleep" a1="60"
Jul 27 17:39:22 myserver tag_audit_log: type=EXECVE msg=audit(1627400360.953:3224545): argc=2 a0="awk" a1=7B2073756D202B3D202431207D3B20454E44207B207072696E7420302B73756D207D
Jul 27 17:39:22 myserver tag_audit_log: type=EXECVE msg=audit(1627400360.943:3224544): argc=5 a0="pgrep" a1="-d" a2=20 a3="--" a4="^qemu(-kvm|:.{1,11})$"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| foreach a*
[| eval test=if(isnull(test),'<<FIELD>>',if(isnull(<<FIELD>>),test,test + " " + '<<FIELD>>')) ]- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Perfect!! 👌🙏
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Think I answered too quickly , for 5 event I have juste one result
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Each event should have its own instance of the test field - by the way, you may want to insert space between each field
| foreach a* [| eval test = if(isnull(test),'<<FIELD>>',test + " " + '<<FIELD>>') ]What else do you have in your search?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for my english...
Maybe I should not use foreach for my search because I would like for x event of type EXEC with the arguments a0 = * a1 = * ect .. which corresponds to a command, concatenate all the arguments to have the complete command
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My search is :
index=linux sourcetype=auditd type=EXECVE
| fields - argc
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your anwser but unfortunately it dosen't work. I havent values for test
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| makeresults
| eval a0="sendmail", a1="-t"
| foreach a*
[| eval test=if(isnull(test),'<<FIELD>>',test + '<<FIELD>>')]Perhaps if you share your real events we might be able to work out why your case doesn't work when this example shows that it does work?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You could try something like:
| foreach a* [| eval test = if(isnull(test),'<<FIELD>>',test + '<<FIELD>>') ]- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This solution work. Thank you