Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why is the cluster search command not returning an...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why is the cluster search command not returning any data?
Hi,
I'm trying to use the Cluster Command to list our Authentication API used by Client IP's. Through searching the events, I already know I have multiple events that are being logged with the same Client IP field. When I try to use the cluster command in my search, I don't get any results. Any and all help would be much appreciated:
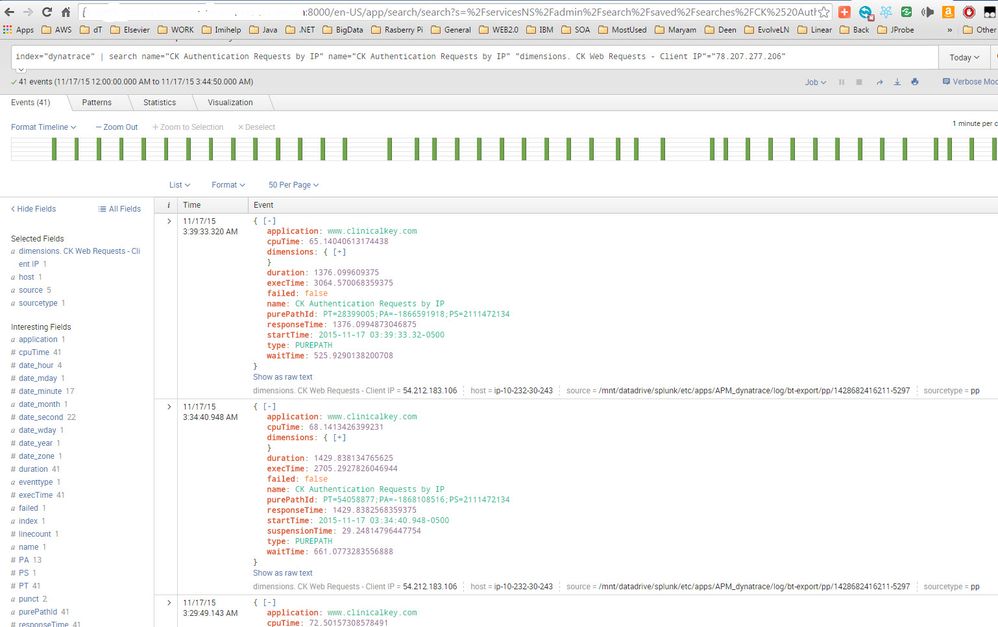
Screenshot of Search without any clustering. I have events with exactly the same IP among non repeating Client IP's:
index="dynatrace" | search name="CK Authentication Requests by IP" name="CK Authentication Requests by IP" "dimensions. CK Web Requests - Client IP"="78.207.277.206"
( I have used a bogus IP and erased the real IP due to my company's rules)
I need help with the Cluster Command Here. It doesn't return any data:
index="dynatrace"| search name="CK Authentication Requests by IP"| cluster t=0.8 showcount=t field="dimensions. CK Web Requests - Client IP" | table name,cluster_count, _raw, "dimensions. CK Web Requests - Client IP" | sort -cluster_count
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure you need to use the cluster command. If all you are trying to do is list all your APIs by IP, try this
index="dynatrace" name="CK Authentication Requests by IP" | stats count by IP
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sundareshr,
I'm only logging all these IP addresses for a single API which is the authentication API. So I need the cluster command to really work as advertised. I do thank you for your earlier answer since I can use it where I have multiple APIs.
Sincerely,
Tahir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI Sundareshr,
Thanks very much for your answer. I'll try it out and will let you know how it works out for me.
Sincerely,
Tahir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi folks,
I have tried all sorts of solutions to no avail. I extracted the client IP into it's own field. I also tried turning it into a string without success, eval client_ip_string=tostring(client_ip)...please see below:
index="dynatrace"| search name="CK Authentication Requests by IP" | eval client_ip_string=tostring(client_ip) | cluster t=0.1 showcount=true field=client_ip_string labelonly=true | table name,cluster_count, "dimensions. CK Web Requests - Client IP" client_ip _raw| sort -cluster_count
In an effort to troubleshoot further, I have tried changing the field param to "name" which is a constant and it shows the cluster command can work but just not on the client IP field. Please let me know if anyone can come up with some other clues.
Sincerely,
Tahir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have been looking at my own problem and found if I at labelonly=true, I start seeing results. I see cluster count if I don't mention the Client IP field. The problem is without mentioning the field I get large bogus numbers for cluster_counts.
Here is the new query with labelonly=true and the mention of a field. BTW the field is a sub-part of a field named dimension.
index="dynatrace"| search name="CK Authentication Requests by IP" | cluster t=0.1 showcount=true field="dimensions. CK Web Requests - Client IP" labelonly=true | table name,cluster_count, "dimensions. CK Web Requests - Client IP" _raw| sort -cluster_count