- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why is my eval command with multiple if conditions...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why is my eval command with multiple if conditions not working?
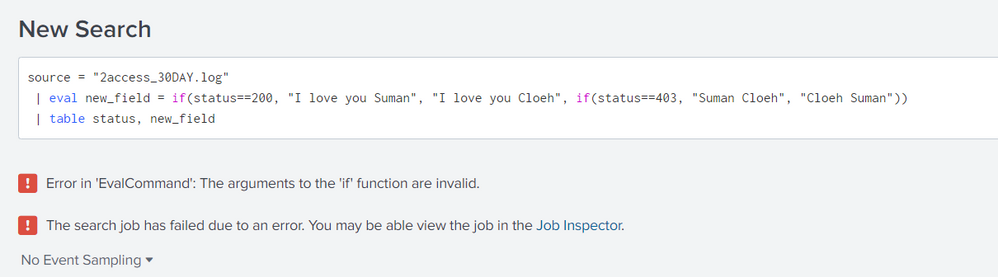
Hi,
I have used eval with multiple if conditions and it's failing. Kindly help.
source = "2access_30DAY.log"
| eval new_field = if(status==200, "I love you Suman", "I love you Cloeh", if(status==403, "Suman Cloeh", "Cloeh Suman"))
| table status, new_field
Suman P.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you have multiple conditions use case not if. Much easer just ensure the last condition is 1==1,"VALUE" if you want a default when nothing before it matches.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @SumanPalisetty ... try the Case Command..
| makeresults |eval status="200"
| eval new_field = case(status==200, "I love you Suman", status==403, "I love you Cloeh",1=1,"Cloeh Suman")
| table status, new_fieldits working perfect.. 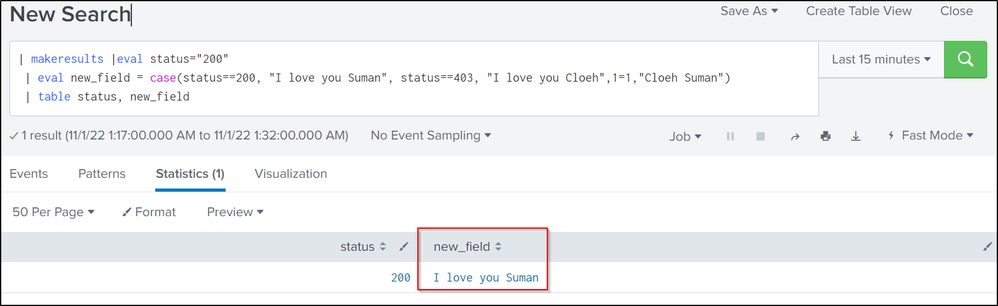
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @inventsekar ,
I want to know what my mistake is, you all being experienced I watt to know where I am making mistake so that i will learn and never repeat it. Thank you.
Regards
Suman P.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
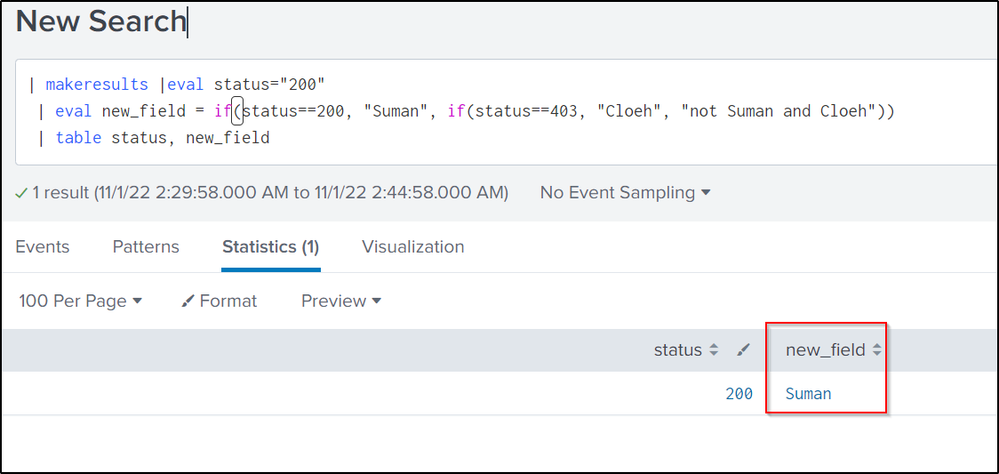
Hi @SumanPalisetty .. the if condition format
if condition is true,
then do this.
or
"do the other"
so, in your if condition.. if status is 200, then suman, .. or, then one more if condition.. like this one:
| makeresults |eval status="200"
| eval new_field = if(status==200, "Suman", if(status==403, "Cloeh", "not Suman and Cloeh"))
| table status, new_field
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @inventsekar ,
Why do we need to add makeresults? Also why do we need to multiple eval commands?
Regards
Suman P.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
on your splunk environment, when you run this,
source = "2access_30DAY.log"
splunk will get the "2access_30DAY.log" log and then the "status" will be analyzed inside the if condition.
but, on my splunk environment, as i dont have the "2access_30DAY.log" log in my system, i should create a temporary variable with eval status="200"... with this i will have a log event and then i can run the if condition. hope you understood now.. let me know if any questions.. as the last reply was working perfectly, please accept it as a solution, so that this question will be moved to unanswered to "answered". thanks.
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your mistake is in the if function - you have more than 3 parameters - have another look at the documentation