Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why is my Lookup search not returning results corr...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why is my Lookup search not returning results correctly?
Hello all,
I am having trouble with a search that is not returning results as it should. The search is below and I have attached an example of the lookup file. When I run a search just looking for an individual IP it does return events but is not working with the lookup file. Any help is appreciated.
index=wineventlog OR index=fortigate
| lookup TORIP TORIP AS src_ip OUTPUT TORIP
| search TORIP=*
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That search seems to be a valid search, but it is looking for all events for all IPs in that index/sourcetype and then retaining only rows that have a src_ip in the lookup file.
What exactly is not working here? Do you have an event with a src_ip that is in the lookup file that is not being shown?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When I run a search for one of the individual ips in the lookup file it returns events.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Isn't that what the search is supposed to do?
So, if you run that search
index=wineventlog OR index=fortigate src_ip=100.14.174.187
| lookup TORIP TORIP AS src_ip OUTPUT TORIP
| search TORIP=*You are saying it returns events?
Can you be more specific in what you are doing and what is occurring that you believe is not correct
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sorry when I run the search I want to look through those two index's for any event that contans at least one of the ip's in the lookup list
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, what does NOT work in that search?
When you run that search like it is, do you get events?
If you get events, are they events for IP addresses in the list or events for IP addresses NOT in the list or do you get no events.
To be able to help, it would be useful if you can describe what you have done and the results you get and the expected results if that is different.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
when I run my original search it gets no events.
when I run the following search with an IP that I know to be in those index's over a period of all time it returns no events
index=wineventlog OR index=fortigate src_ip=100.14.174.187 | lookup TORIP TORIP AS src_ip OUTPUT TORIP | search TORIP=*
when I run the following search it looks like its just returning any event that has a src_ip in it not just whats in the lookup file
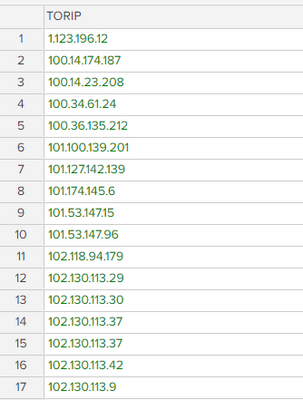
index=wineventlog OR index=fortigate [| inputlookup TORIP |rename "TORIP" as "src_ip" |return 999 "src_ip"]
my hope was to run the search every 24 hrs and return all events that match an IP in the lookup file.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, this search returns NO events?
index=wineventlog OR index=fortigate src_ip=100.14.174.187or after you add
| lookup TORIP TORIP AS src_ip OUTPUT TORIP
| search TORIP=*you get no results?
If after the initial phase, then there is no event with a field src_ip as that value, either because it does not exist, or src_ip is not a valid field with that value.
If after the second, there is an issue with the lookup.
The reason the second is returning all IPs is because that evaluated search looks like this
index=wineventlog OR index=fortigate (src_ip="IP_1") OR (src_ip="IP_2") OR ...which means that you will get ANY event from index=wineventlog OR ANY event from index=fortigate WHERE src_ip matches the set of IPs. - Brackets needed round the index statements.
I assume this statement works and returns all IPs in the lookup file?
| inputlookup TORIP
| search TORIP=*
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @tkerr1357
Try this search and see if it produces the data you're looking for.
index=wineventlog OR index=fortigate
[| inputlookup TORIP |rename "TORIP" as "src_ip" |return 999 "src_ip"]- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the search worked but seems like its returning all IPs not just the ones in the lookup file.