Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why are my props/transforms not taking effect?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why are my props/transforms not taking effect?
Hello, i have a single Splunk Enterprise instance with a 9997 listener. I have a single Windows Server with a UF forwarding data to the Splunk Enterprise. This is all good; data is being forwarded as expected.
I am now trying to make a few props.conf changes to the data, but none of my configuration seems to make any difference, when i go look in the Splunk Enterprise search app.
Here in props.conf i a, trying to transform the host, set the timezone to Sydney and set the event time.
[WinEventLog:*]
TRANSFORMS-change_host = WinEventHostOverride
TZ = Australia/Sydney
DATETIME_CONFIG = CURRENT
Here in transforms.conf is my host overide block;
[WinEventHostOverride]
DEST_KEY = MetaData:Host
REGEX = (?m)^ComputerName=([\S]*)
FORMAT = host::$1
On every change i make, i have performed a splunk.exe restart on the UF host. However, nothing appears to change in my index.
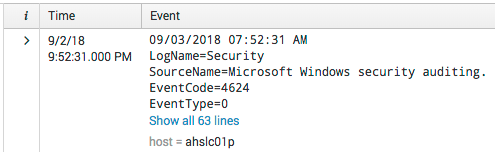
Here is a sample from my index.
- As you can see the
Timefield is UTC, but i want the time in the actual Event to be the Time. - The
hostfield is not transforming to the correct ComputerName field in the event.
Using Answers from other questions, i used the following search query to "test" the regex and it appears to work, so i am confused why it doesn't work.
index=* | head 1 | eval testdata="ComputerName=ahslc01p" | regex testdata="(?m)^ComputerName=([\S]*)" | stats count
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks to both of you. The Wiki article is invaluable, and should be re-incorporated into official documentation.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A two things I can spot:
- in
props.confyou are using a*in the sourcetype name, this is not supported. - you restarted the UF after each change - but the props/transforms should be applied on your single Splunk instance
cheers, MuS
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yep, this is a slightly old piece of documentation, but it gives a good understanding of what goes where, in terms of configuration items.
https://wiki.splunk.com/Where_do_I_configure_my_Splunk_settings%3F
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, this Wiki was invaluable and should be incorporated back into official documentation.