- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why am I unable to extract cookie field?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why am I unable to extract cookie field?
So I'm trying to extract a field called "secureToken=tokenvalue" from our akamai logs. However when I try to extract the field, it gives me the following error message:
The extraction failed. If you are extracting multiple fields, try removing one or more fields. Start with extractions that are embedded within longer text strings.
I have attempted to manually edit the regex, but I have not a lot of experience with regex so any help would be greatly appreciated
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay great!
However, I want to extract the "secureToken" bit from the following:
Set-Cookie: secureToken=11111112222233333445; Path=/; Secure; HttpOnlySo I can add add it into the interesting fields section when searching in splunk
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I really don't understand you? I just gave you the answer on a silver platter wrapped in a gold bow tie....
Do you actually understand my answer or are you trolling me?
The following spl command will extract the secureToken value and create a field called secureToken.
| rex "secureToken=(?<secureToken>\d+)"
If you still don't understand I suggest you take the splunk course: https://www.splunk.com/en_us/training/courses/using-fields.html
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I get it now don't worry, I was just a bit slow that is all!
Thank you for your help
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
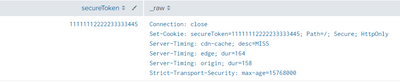
Connection: close
Set-Cookie: secureToken=11111112222233333445; Path=/; Secure; HttpOnly
Server-Timing: cdn-cache; desc=MISS
Server-Timing: edge; dur=164
Server-Timing: origin; dur=158
Strict-Transport-Security: max-age=15768000
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This works as a basic example:
| makeresults | eval _raw="Connection: close
Set-Cookie: secureToken=11111112222233333445; Path=/; Secure; HttpOnly
Server-Timing: cdn-cache; desc=MISS
Server-Timing: edge; dur=164
Server-Timing: origin; dur=158
Strict-Transport-Security: max-age=15768000"
| rex "secureToken=(?<secureToken>\d+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi thanks for the reply!
I just want to extract the secureToken field though.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To make it more clear how a regular expression field extractions works:
The rex syntax:
rex field=<field> <PCRE named capture group>
The PCRE named capture group works the following way:
(?<name>regex)
The above expression captures the text matched by regex into the group name.
If you don’t specify the field name, rex applies to _raw (which is the entire event).
Another example to make it more clear:
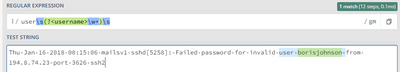
My example event is:
Thu Jan 16 2018 00:15:06 mailsv1 sshd[5258]: Failed password for invalid user borisjohnson from 194.8.74.23 port 3626 ssh2
I want to extract the username from this:
I do that with:
index=test sourcetype=demo_events
| rex user\s(?<username>\w+)\s
This will create the field name username with the extracted value of borisjohnson
From regex101:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did exactly that in my reply with the part:
| rex "secureToken=(?<secureToken>\d+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please provide a couple of sample events.