- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Why am I unable to extract all fields from a C...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why am I unable to extract all fields from a CSV log in Splunk 6.2.5?
I'm trying to extract fields from a basic .csv log with no luck.
Here is the file how it looks in Splunk 6.2.5..
When I try to configure a field extraction, Splunk only recognizes the very first instance....
Any help would be greatly appreciated - thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In props.conf you need KV_MODE=multi
- Used for search-time field extractions only.
- Specifies the field/value extraction mode for the data.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
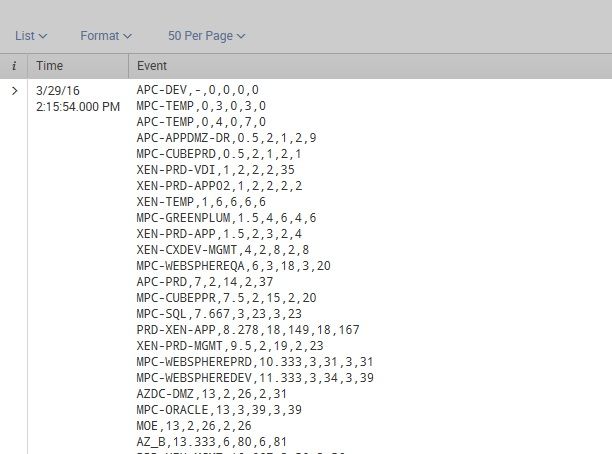
The data is being loaded into a single event.
Should it break thusly?
3/29/2016,APC-DEV,-,0,0,0,0
3/29/2016,MPC-TEMP,0,3,03
If that's so, please let me know...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, This is how I would like to see the log file break....
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
got it....that's the problem, need to break after the carriage return.
1) When you ingest the file, you need to create a new custom sourcetype.
2) in $splunk/etc/apps/search/local .... you'll see that new sourcetype referenced.
3) you need to instruct splunk to break after each line: LINE_BREAKER = ([\r\n]+)
...or the props.conf on the deployment server should work as well....
http://docs.splunk.com/Documentation/Splunk/6.2.5/Data/Indexmulti-lineevents
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume you are using rex so you need to use the max_match=0 option.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Should this option be added to the props.conf located here: /opt/splunk/etc/deployment-apps/app_common/local ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You did not mention props.conf in your question so we had to guess. That is why it is important to clearly spell out what you have done so far. No, max_match is not part of the props.conf way of extracting fields. I will post another answer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you go to production yes, tthe props.conf will then get sent to the forwarder that is collecting the data.
But for now you can test in : in $splunk/etc/apps/search/local .. and local the file a local directory to test...does that make sense?