Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- What time should be when searching old logs?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dujas
Explorer
02-15-2023
06:53 AM
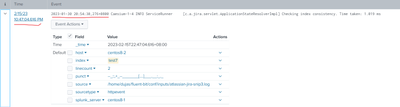
I am using Splunk searching old log files and the _time is different from log time, would this make sense or do I have to parse the log to set _time to log time?
Thanks.
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gcusello

SplunkTrust
02-15-2023
07:04 AM
Hi @dujas,
yes, usually the event timestamp (_time) is the same of the event.
You have to better parse your logs to have as timestamp, the event timestamp.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gcusello

SplunkTrust
02-15-2023
07:04 AM
Hi @dujas,
yes, usually the event timestamp (_time) is the same of the event.
You have to better parse your logs to have as timestamp, the event timestamp.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dujas
Explorer
02-18-2023
02:03 AM
Thanks @gcusello , I have parsed the log line and made it work.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gcusello

SplunkTrust
02-18-2023
03:29 AM
Hi @dujas,
good for you, see next time!
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated 😉
Get Updates on the Splunk Community!
CX Day is Coming!
Customer Experience (CX) Day is on October 7th!!
We're so excited to bring back another day full of wonderful ...
Strengthen Your Future: A Look Back at Splunk 10 Innovations and .conf25 Highlights!
The Big One: Splunk 10 is Here!
The moment many of you have been waiting for has arrived! We are thrilled to ...
Now Offering the AI Assistant Usage Dashboard in Cloud Monitoring Console
Today, we’re excited to announce the release of a brand new AI assistant usage dashboard in Cloud Monitoring ...