Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- VT4Splunk APP correlation with paloalto
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VT4Splunk APP correlation with paloalto
Hi, I have installed the virustotal add-on for Splunk.
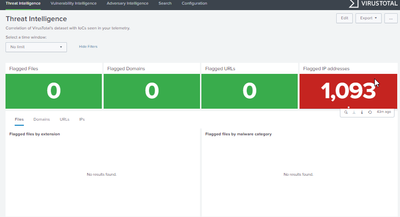
When I enter the dashboards that are already pre-built I find that the data is related to .csv files.
When I enter one of the panels to see how the query is constructed I see that it is indeed a list of IP address values and a reputation level given by virustotal.
| inputlookup vt_ip_cache | search vt_detections > 0 | where "1" = "1" OR _first_seen_in_events >= relative_time(now(), "1") | stats count
I am currently on a license of X amount of GB which I am using to ingest logs from many windows machines and some Azure services so I am getting the firewall logs in Elasticsearch and I use the command
| ess eaddr="http://localhost:9200" index=paloalto* tsfield="@timestamp" query="*" fields="SourceIP"Each query independently brings me results, but what I need is to correlate the virustotal source logs on the IP addresses where the field is called vt_id and show only the ones that match the logs from the paloalto under the SourceIP field
I am not very skilled with this type of queries and for this reason I ask for your help, I managed to build this query, which does not bring me results either because there are no matches or because it is incorrect, what do you think?
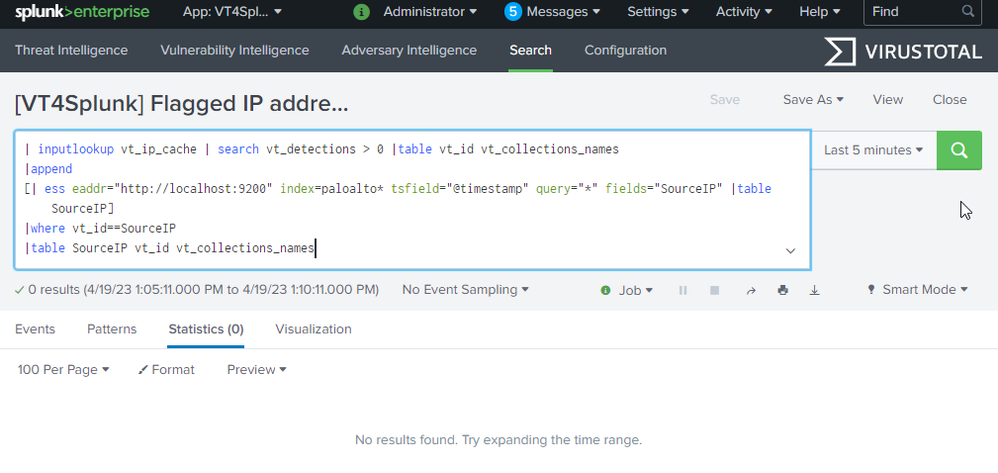
| inputlookup vt_ip_cache | search vt_detections > 0 |table vt_id vt_collections_names
|append
[| ess eaddr="http://localhost:9200" index=paloalto* tsfield="@timestamp" query="*" fields="SourceIP" |table SourceIP]
|where vt_id==SourceIP
|table SourceIP vt_id vt_collections_namesWould you help me to adjust or improve it?
thanks