Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Use of _indextime field in table or stats command
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Use of _indextime field in table or stats command
Hi All
How can I use _indextime field in table or stats command without renaming or converting it.
Not working
Ex: * | table host source sourcetype _time _indextime _raw
Its working if I rename the _indextime or convert the _indextime, But I want the results with _indextime as field
Working
Ex: * | eval indextime=_indextime | table host source sourcetype _time indextime _raw
Thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rakshithreddy,
_indextime is an internal filed and a hidden field, it will not be displayed in search results unless renamed or used with an eval.
So whenever you eval _indextime it will work.
Please refer below document for more information.
http://docs.splunk.com/Documentation/Splunk/7.0.0/Knowledge/Usedefaultfields
Thanks
Happy Splunking
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
Thanks for reply
We can display _raw , _time not _indextime & not sure why
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rakshithreddy,
Good question.
_raw and _time is NOT hidden field.
The _raw field contains the original raw data of an event. The search command uses the data in _raw when performing searches and data extraction.
The _time field contains an event's timestamp expressed in Unix time. This field is used to create the event timeline in Splunk Web.
_indextime is a hidden field that's why we have to eval _indextime to make in use.
🙂
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good to know,
But I was looking for anyway if we cheat this thing.
Thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rakshithreddy,
Yes, for you I have a trick but in configuration.
If we set EVAL in props.conf then we don't need eval in any search in the app.
Just put below configuration in props.conf.
[MY_SOURCETYPE]
EVAL-indextime=_indextime
Search:
sourcetype=MY_SOURCETYPE | table _time indextime
Thanks
Happy Splunking.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try please - base search | eval indextime=strftime(_indextime,"%Y-%m-%d %H:%M:%S") | table indextime
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks for reply,
I want it to be -
base search | table _indextime, the field name should be _indextime as i am sending these results to an external application & that application can only detect if its _indextime
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
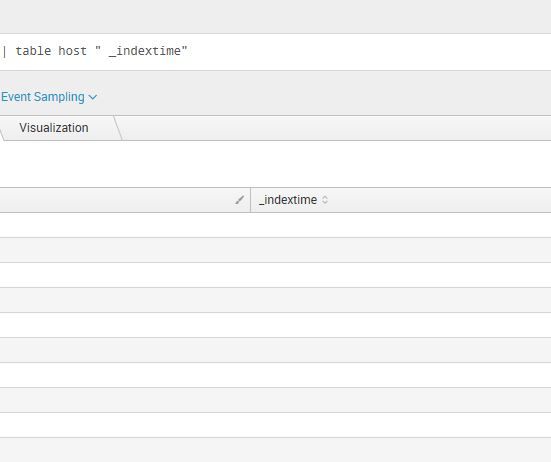
I think you're out of luck. You can't display exact "_indextime" as the output will always filter.
You can fake it and put in a space though.
index=_internal | rename _indextime AS " _indextime"| table host " _indextime"
Notice the space in the quotes.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content