Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Tracking failed logins followed by successful ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tracking failed logins followed by successful logins using the transaction command
Hello,
I am trying to track failed logons followed by a successful one using the transaction command and the following criteria:
Limit the time span to 5 min, add a startswith so each transaction will begin with a logon failure, add an endswith so each transaction will end with logon success and add a | where to find when the eventcount exceeds 3
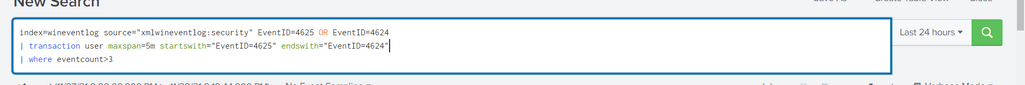
this is what I have so far
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @My,
I don't like transaction command and I use it only when I haven't any other solution.
In your case, you could do this:
index=wineventlog sourcetype=xmlwineventlog:Security EventCode IN (4624,4625)
| stats dc(EventCode) AS dc_eventcode count(eval(EventCode=4625)) AS failed BY user host
| where dc_eventcode>1 AND failed>5in this way you have the filter for more than 5 failed logins and a successful login grouped for user and host.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't see what's wrong with this, except that I don't understand the "where eventcount >3". Without that I expect that it should give you the right results. Or what is it exactly that you are missing?