Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Timechart not working for 30days and more
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Timechart not working for 30days and more
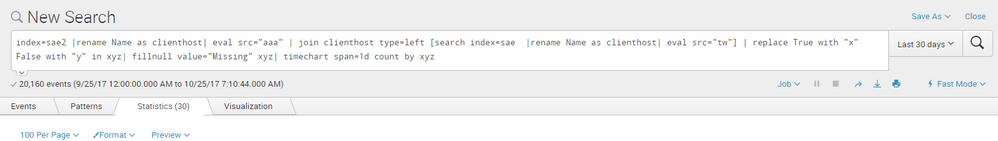
My timechart is working perfectly for last 10 days but it is not working for time range above 15 days.Any idea to resolve this?
please find the screenshot of the query.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@nivethainspire_07, do you really need join? I dont see the need for creating src field (you have not used it afterward). replace and fillnull can be placed after the transforming command so that they operate on aggregated field/s. Please try out the following instead:
index="sae2" OR index="sae"
| timechart count by xyx
| replace "True" with "x" "False" with "y"
| fillnull value="Missing" xyz
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
do you get an error in the Job dropdown? Anything about subsearch timeout or truncating because of too many events? could you try rewriting the query to see if that helps?
index=sae2 OR index=sae
|rename Name as clienthost
|eval src=if(index="sae2","aaa","tw")
|replace True with x False with y in xyz
|fillnull value="Missing" xyz
|timechart span=1d count by xyz
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please tell me how it will not move.
For example, is the limit of maxout of sub search OK?
http://docs.splunk.com/Documentation/Splunk/6.6.3/Admin/Limitsconf