- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Splunk 6.6.2: Why is inputting the token porti...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk 6.6.2: Why is inputting the token portion of the search and adjusting the source code within the dashboard, does not display the same data?
Hello
I am wondering why when I search with the original query it pulls all of the data I want and displays it the way I want.
product=Windows status=failure Failure_Reason="*" Account_Name=$Account_Name_token$ | stats count by Failure_Reason, Status, Workstation_Name | sort - count |
However, when I input the token portion of the query and adjust the source code within the dashboard it does not display the same data?
"Account_Name=$Account_Name_token$" should not remove data right? This makes no sense to me
Attached is a picture of what the dashboard source code looks like.
I have reviewed the documentation.
I can tell you that the Splunk instance is on 6.6.2 and not 7.1 (client has been informed of this) and if that is the overriding issue obviously they need to upgrade.
I appreciate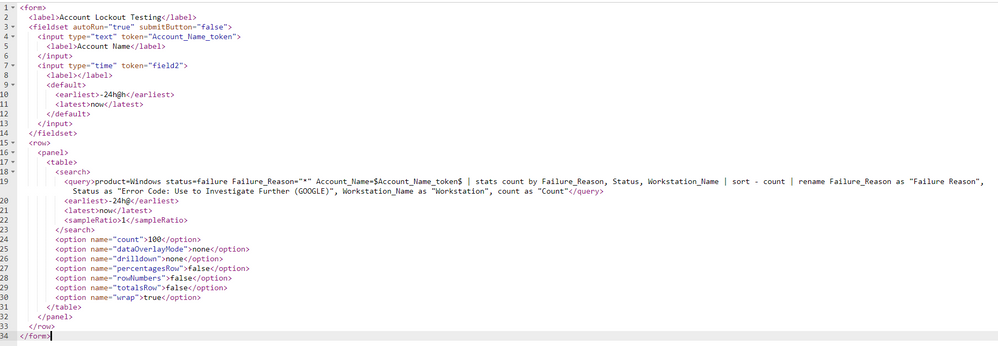
Thank you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Hegemon76 ,
Did you have a chance to check out an answer? If it worked, please resolve this post by approving it! If your problem is still not solved, keep us updated so that someone else can help you.
Thanks for posting!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The only person who responded to this was me.....
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No one has seen this issue before? Geez
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correction
The original query looks like this
product=Windows status=failure Failure_Reason="*" | stats count by Failure_Reason, Status, Workstation_Name | sort - count |
I add in "Account_Name=$Account_Name_token$" once the dashboard has been made.
