Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Single Value Color Change
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a panel that is a single value that only shows the Health Status as "UP" or "DOWN". If it is "UP" I want it to be green. If it is "DOWN" I want it to be red.
How can I do this in the source code?
This is a query the shows what the panel is doing.
index=index_name
| rename msg.event.healthStatus as healthStatus
| dedup healthStatus
| table healthStatus
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please try this?
<dashboard>
<label>Up_Down_single_View</label>
<row>
<panel>
<single>
<search>
<query>index=index_name
| rename msg.event.healthStatus as healthStatus
| dedup healthStatus
| table healthStatus | eval severity=if(healthStatus ="UP",1,4) | rangemap field=severity low=0-2 default=severe</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</single>
</panel>
</row>
</dashboard>
Thanks
KV
▄︻̷̿┻̿═━一
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Close, but not exactly there. It's one panel.
This query
index=index_name
| rename msg.event.healthStatus as healthStatus
| dedup healthStatus
| table healthStatus
The table will only show the healthStatus. healthStatus will only equal UP or DOWN. If the value of healthStatus is UP, I want the word UP to be green. If the value of healthStatus is DOWN, I want it to be RED. Only one value will be displayed at a time because I want it to be a single value display.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please try this?
<dashboard>
<label>Up_Down_single_View</label>
<row>
<panel>
<single>
<search>
<query>index=index_name
| rename msg.event.healthStatus as healthStatus
| dedup healthStatus
| table healthStatus | eval severity=if(healthStatus ="UP",1,4) | rangemap field=severity low=0-2 default=severe</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</single>
</panel>
</row>
</dashboard>
Thanks
KV
▄︻̷̿┻̿═━一
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
may be rangemap will help you.
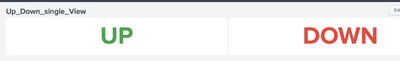
Can you please try this?
<dashboard>
<label>Up_Down_single_View</label>
<row>
<panel>
<single>
<search>
<query>| makeresults | eval value="UP" | table value | eval severity=if(value="UP",1,4) | rangemap field=severity low=0-2 default=severe</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</single>
</panel>
<panel>
<single>
<search>
<query>| makeresults | eval value="DOWN" | table value | eval severity=if(value="UP",1,4) | rangemap field=severity low=0-2 default=severe</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</single>
</panel>
</row>
</dashboard>
Important links:
https://docs.splunk.com/Documentation/Splunk/8.2.0/SearchReference/Rangemap
Thanks
KV
▄︻̷̿┻̿═━一
If any of my reply helps you to solve the problem Or gain knowledge, an upvote would be appreciated.