Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Searching EventCodes for logon and logoff even...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Searching EventCodes for logon and logoff events, LOGON_ID includes 0x0 before actual LOGON_ID. How do I exclude the 0x0?
I am trying to build a report that shows how long a user was logged on. To do this, I am trying to match LOGON_IDs for the logon and logoff events. Here's my search code:
((EventCode=4624) OR (EventCode=4634)) AND (Account_Name="ADnowens") |Transaction Logon_ID startswith=4624 endswith=4634 | eval SessionLength= tostring(round(duration/1000,0), "duration") | search SessionLength!="00:00:00" | table host Account_Name SessionLength _time
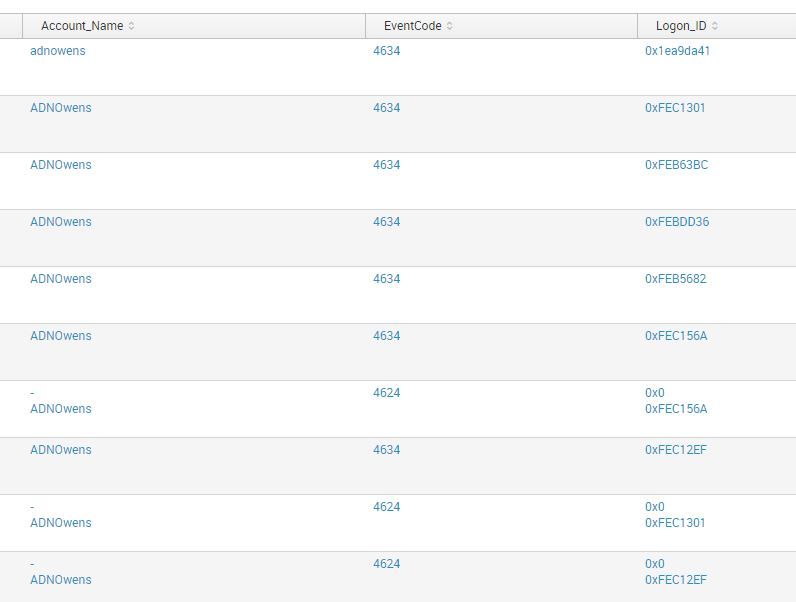
The problem I am having is that many of the LOGON_IDs have 0x0 before the actual LOGON_ID on the 4624 events. The logoff 4634 doesn't have these so they don't match and the report is not catching them. Any idea how to exclude the 0x0 in the comparison?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| eval logid=mvindex(Logon_ID, 0) - das erste von oben nach unten gesehen
| eval logid=mvindex(Logon_ID, 1) - das zweite
| eval logid=mvindex(Logon_ID, 2) - das dritte
| eval logid=mvindex(Logon_ID, 3) - das vierte
mit mvindex legt man fest welches der erkannten Werte genommen werden soll.
Wenn ich mich recht entsinne sollte es bei dir
| eval logid=mvindex(Logon_ID, 1) sein da die User Logon_ID als zweites kommt.
Gruß Micki
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, you have some Logon_ID's that are like 0x0123456 and others that are 123456?
((EventCode=4624) OR (EventCode=4634)) AND (Account_Name="ADnowens") |
rex mode=sed field=Logon_ID "s/^0x0//" |
Transaction Logon_ID startswith=4624 endswith=4634 |
eval SessionLength= tostring(round(duration/1000,0), "duration") |
search SessionLength!="00:00:00" |
table host Account_Name SessionLength _time
See if that helps.
My Logon_IDs have "0x" in front of them, not "0x0" so that in my case is "s/^0x//" instead of "s/^0x0//".
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it working guys. Thanks for the help!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great! I was about to come in and make some more comments, but found I didn't need to!
Could you post what you did to solve/resolve it for others to be able to see what the fix was? Please, accept this answer with additional comment) if it was a really large part of the answer you needed, but feel free if you solved it in a different way entirely to post your OWN answer and mark it as the answer. That's totally OK as long as it's legit!
And thanks to helping to make the community better!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So it seems my issue now may be with determining the SessionLength. Rich's solution does seem to remove the 0x0 but my sessionlength is not working correctly. ANy thoughts on what's the best way to determine the time difference between to two events with the same Logon_ID?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi neiowe
If you're trying to remove 0x0 rich7177's answer should work.
| rex mode=sed field=Logon_ID "s/^0x0//"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I get the exact smae results with or without the | rex mode=sed field=Logon_ID "s/^0x0//" in the search. The screen shots I posted below shows the Logon_IDs. It appears there may be a CR between the 0x0 and the Logon_ID for the 4624 events that would match the Logon_ID for the 4634 event.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content