Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- SPL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
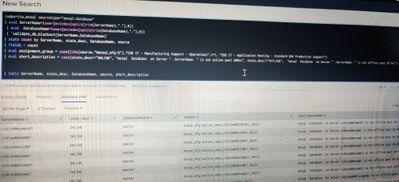
SPL
How can i use multiple NOT condition in my second eval function. My attribute is there state_desc!="ONLINE" OR state_desc!="OFFLINE"
In above condition i always returned only first value not for the second one.
Is need to use LIKE , match or any other command because result is in string .please suggest
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I understand the question, I think the issue is that you are using ! which means "state_desc (IS NOT) = "ONLINE" in all of the case statements
try this, and see if it addresses your needs:
|eval short_description=case(short_desc="OFFLINE","system is offline", short_desc="SUSPECT","system is suspect", short_desc="Recovery pending", "system is recovering", 1=1, "System is Online")
|eval isAlert=if(short_desc!="ONLINE",1,0)
The fist eval populates "short_description" with a description of each state.
The second eval creates a new field called "isAlert". For any condition where the short_desc does not contain "ONLINE" it will return a 1, but for a normal online condition it will contain a 0
If your aim is to fire an alert for an abnormal condition, you only need to worry about results in which isAlert=1, so adding
|search isAlert=1
at the end will only show you results which indicate the system was not reporting "ONLINE"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@nickhills Yes i am agree, because multiple NOT condition in case statement are causing issue and all the not condition are consider only !=ONLINE condition value and create only single value.
Let me try your suggested SPL, i will let you know if this work.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| eval sample=if(match(state_desc,"(ON|OFF)LINE"),"nothing", "what you want")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@to4kawa For multiple Not condition how match will work. Match command only work for true value. Please suggest when condition is not matched as suggested below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| makeresults
| eval Alpha=split("ABCDEFGHIJKLMNOPQRSTUVWXYZ","")
| mvexpand Alpha
| where NOT (Alpha="A" OR Alpha="C" OR Alpha="X" OR Alpha="Z")- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not quite clear that I understand your issue.
Is there a reason you are using ! and CASE?
If there are only two options for the value of state_desc you could use "IF" and avoid the !
|eval state_description=if(state_desc="ONLINE", "system is online","system is offline")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
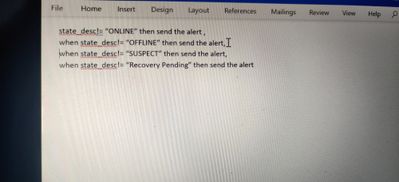
For below requirement i am use the case statement with ! Condition. Please assist.