Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Regex Issue using Rex command?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regex Issue using Rex command?
Hi,
I have a field X with values similar to the following "device-group APCC1_Core_Controller pre-rulebase application-override rules NFS-bypass UDP-1" and "device-group APCC1_Core_Controller pre-rulebase application-override rules" as 2 examples of possible values.
I need to extract the value in between "device_group" and "per_rulebase...." and assign this as Y.
So, if X = "device-group APCC1_Core_Controller pre-rulebase application-override rules NFS-bypass UDP-1"
=> Y = "APCC1_Core_Controller"
If X = "device-group APCC1_Core_Controller pre-rulebase application-override rules"
=> Y = "APCC1_Core_Controller".
What would the rex command be???
Thanks,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
At the moment, I have got this far:
However, I do not want to have "device-group:" included as part of the values.
How can I change my regex?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you don't want device-group, don't include it in the parenthesis. Also, \w is incorrect for your data because your group name often includes dashes as illustrated. See my other post.
| rex "device-group (?<device_group>\S+)"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
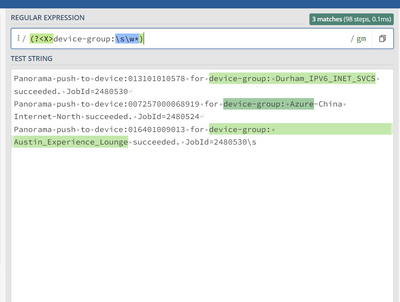
So, say I have a field called "M" and some of the values are as follows:
"Panorama push to device:013101010578 for device-group: Durham_IPV6_INET_SVCS succeeded. JobId=2480530"
"Panorama push to device:007257000068919 for device-group: Azure-China-Internet-North succeeded. JobId=2480524"
"Panorama push to device:016401009013 for device-group: Austin_Experience_Lounge succeeded. JobId=2480530"
How can I extract just the first string in between each "....device-group: *** succeeded. ....", where *** represents the respective value to be extracted. In the case of the above 3 examples, the 3 values extracted are "Durham_IPV6_INET_SVCS", "Azure-China-Internet-North" and "Austin_Experience_Lounge" respectively.
I tried using the following Splunk command but got no success 🙄:
|rex "body\s(?<portNumber>\d+)\s"
Any help?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, there's a colon after "device-group". So add that.
| rex "device-group: (?<device_group>\S+)"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, say I have a field called "M" and some of the values are as follows:
"Panorama push to device:013101010578 for device-group: Durham_IPV6_INET_SVCS succeeded. JobId=2480530"
"Panorama push to device:007257000068919 for device-group: Azure-China-Internet-North succeeded. JobId=2480524"
"Panorama push to device:016401009013 for device-group: Austin_Experience_Lounge succeeded. JobId=2480530"
How can I extract just the first string in between each "....device-group: *** succeeded. ....", where *** represents the respective value to be extracted. In the case of the above 3 examples, the 3 values extracted are "Durham_IPV6_INET_SVCS", "Azure-China-Internet-North" and "Austin_Experience_Lounge" respectively.
I tried using the following Splunk command but got no success 🙄:
|rex "body\s(?<portNumber>\d+)\s"
Can you please help?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
regex101: build, test, and debug regex
Please take a look at this link. I suggestion use regex101 before put them into splunk.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. What have you tried yourself?
2. Can you provide the full event so that I can make an example for you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The full event is as follows:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
extract the value in between "device_group" and "per_rulebase...." and assign this as Y
I speculate that "per_rulebase" is a mistype for "pre_rulebase" as mentioned elsewhere in the OP. The problem is that this "pre_rulebase" or "per_rulebase" does not seem to be a literal string, according to the sample event; it appears to be an application/industry specific term related to this source, something like "with merge-with-candidate-cfg flags". If this correct, you cannot expect people in a Splunk forum to intuit what "pre_rulebase" (or per_rulebase) stands for.
On superficial observation, the "Y" you are trying to extract is really just the name of device group. If this name cannot contain spaces, you can simply do
| rex "device_group (?<device_group>\S+)"If the name may contain space, but the "pre_rulebase" always begins with keyword "with" as exemplified in the sample event, you can do something like
| rex "device_group (?<device_group>.+) with "Of course, this second form has a larger chance of overreaching because the word "with" may appear in some other content of the event. You have to find some pattern to reduce such chances.