Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Question about subsearch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
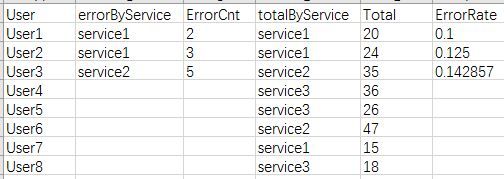
I have below query and the results like below table, is there a way that only search and display total count for the Users who have error(User1, User2, User3)?
index=aaa sourcetype=bbb |eval errorByService=case(ErrorCode=400 AND match(uri,"/service1/*"),"service1",ErrorCode=400 AND match(uri,"/service2/*"),"service2",ErrorCode=400 AND match(uri,"/service3/*"),"service3")|stats count as ErrorCnt by User errorByService
|appendcols [search index=aaa sourcetype=bbb |eval totalByService=case(match(uri,"/service1/*"),"service1",match(uri,"/service2/*"),"service2", match(uri,"/service3/*"),"service3")|stats count as Total by User totalByService] |eval ErrorRate=ErrorCnt/Total |fields User, errorByService, ErrorCnt, totalByService, Total, ErrorRate
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is possible with ”addcoltotals” if you add a field for calculation.
(your search)
|eval Error=if(isnull(ErrorCnt),0,1)
|addcoltotals labelfield=User label=TOTAL Error
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is possible with ”addcoltotals” if you add a field for calculation.
(your search)
|eval Error=if(isnull(ErrorCnt),0,1)
|addcoltotals labelfield=User label=TOTAL Error
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi HiroshiSatoh,
Thank you for your answer. Maybe there is a ambiguity for my question. My question is if it possible the User range for subsearch is only for those user who have error.
In subsearch, it searched all Users' data, the results shows the "Total" for User1, User2...User8, but only User1,User2, User3 have error, I want to only search and show "Total" for User1,User2, User3 in subsearch, is it possible?
Expected results:
User errorByService ErrorCnt totalByService Total ErrorRate
User1 service1 2 service1 20 0.1
User2 service1 3 service1 24 0.125
User3 service2 5 service2 35 0.142857143
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm sorry I do not understand what I want to do.
If only to extract
(your search)
|where where isnotnull(ErrorCnt)
If conditional summary ex・・・
|stats sum(eval(if(isnotnull(ErrorCnt), Total,0))) AS Total