- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Query syslog fields
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear all,
I have a syslog-ng relay server collecting syslog messages from remote network devices and saving them as log files. Then I have Splunk UF forwarding this data to the splunk cloud. Following is a sample message
May 30 04:23:54 192.168.1.132 <82>May 30 04:23:54 syslog-data-generator-01 This is a test message from b001-491 2021-05-30T04:23:54.116Z
And following is my inputs.conf
[monitor:///var/log/remotelogs/]
disabled = 0
sourcetype = syslog
I can see the messages collected from splunk cloud by querying _raw
My question: How would I write a query to display [data, host, facility, severity, message]
Many thanks in advance
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
host is already extracted so you might want to use a different name
| rex "(?<date>\w+\s\d+\s\d\d:\d\d:\d\d)\s(?<host>[^\s]+)\s<(?<severity>\d+)>(?<msg>.*)"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @ITWhisperer ,
Thank you for taking time to read my question and respond
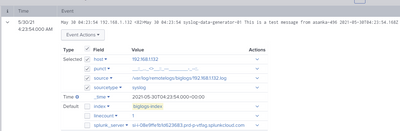
Following is what I see
sample message
May 30 04:23:54 192.168.1.132 <82>May 30 04:23:54 syslog-data-generator-01 This is a test message from asanka-496 2021-05-30T04:23:54.168Z
screen-shot
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So which part of the message is which?
May 30 04:23:54 192.168.1.132 <82>May 30 04:23:54 syslog-data-generator-01 This is a test message from asanka-496 2021-05-30T04:23:54.168Z
data or date?
host
facility
severity
message
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
typo date should be date
May 30 04:23:54 - date
192.168.1.132 - host
<82> - PRI (facility, severity)
Rest is the message
Cheers
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
host is already extracted so you might want to use a different name
| rex "(?<date>\w+\s\d+\s\d\d:\d\d:\d\d)\s(?<host>[^\s]+)\s<(?<severity>\d+)>(?<msg>.*)"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you are awesome mate !!!!!!! thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is the example you shared, the _raw message you get when searching your index?
Do you have any interesting fields already extracted for you?
Which part of the message do you want in data(?) host facility etc i.e can you provide a corresponding example of the expected output?