Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Need help selecting values from two events and cal...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
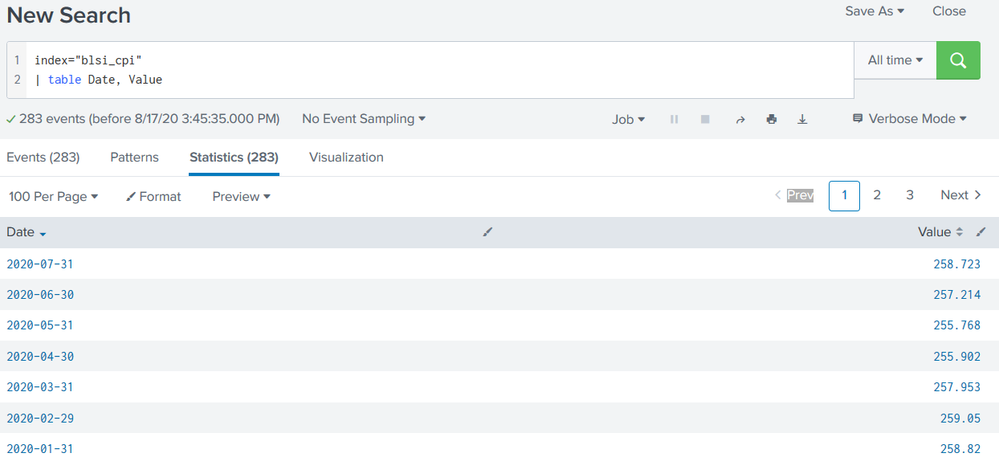
First of all, thanks for any help you may be able to give me. I would appreciate some help with a problem I'm having. I uploaded a csv file to my Splunk that contains only Date/Value pairs. Below is an example of the data.
I would like to select the Value of 2020-07-31 and the value of 2020-06-30 and calculate the percentage change over that month. Additionally, I'd like to be able to calculate the percentage change but I think I may be able to get that on my own if I can get a hand with the first part.
I'd share my queries so far but I wasted the whole day yesterday trying to get this to work with little useful progress.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, I decided to fix how I ingested the data in the first place to make the Date column the timestamp. I added TIMESTAMP_FIELDS and FIELD_FORMAT to the conf file. This greatly simplified my queries. This is probably the right solution for me instead of doing something wrong and then making a convoluted workaround. Thanks for the suggestion.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Below query shall give you output of your first question. You need to use where clause in your query. Do let me know if you need more help. Hit a like answer was helpful.
index="blsi_cpi"|table Date, Value|where Date="2020-07-31" or Date="2020-06-30"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| gentimes start=01/31/2020
| eval _time=starttime
| timechart span=1month count
| eval _time=relative_time(_time,"-1d@d")
| reverse
| eval Value=100
| streamstats count
| eval Value=Value+count*45
| fields - count
| rename COMMENT as "this is sample"
| rename COMMENT as "this is logic"
| reverse
| autoregress Value as last_Value
| reverse
| eval perc=round(Value/last_Value * 100,2)You didn't provide a calculation method, so I'm not sure.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, I decided to fix how I ingested the data in the first place to make the Date column the timestamp. I added TIMESTAMP_FIELDS and FIELD_FORMAT to the conf file. This greatly simplified my queries. This is probably the right solution for me instead of doing something wrong and then making a convoluted workaround. Thanks for the suggestion.