- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Mapping the location of a TrueClientIP on a Cluste...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible to Map out the locations of the 'TrueClientIP' Field in a search using either a Cluster or Choropleth Map.
I have the below Search that shows me any website activity with an "UNKNOWN" Redirect URL and "UNKNOWN" Cookie Date and would like to Chart the location of where the TrueClientIP is coming from/based (Public IP).
sourcetype=iis CookieData="\"UNKNOWN\"" RedirectTo="\"UNKNOWN\"" TrueClientIP!="\"UNKNOWN\"" TrueClientIP!="\"127.0.0.1\"" | timechart minspan=1h count by TrueClientIP limit=5 usenull=f useother=f
Are you aware of a way that Splunk can pick up the location of a Public IP by its IP Address? Is there any third party apps etc. or way I can link this Data into my search and show this on a Map.
Regards
Jonathan
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
You could try using a combination of iplocation and geostats to generate a report.
Here's an example.
This first part is just to create a result to test with (you'd use the actual data from your search):
| makeresults
| fields - _time
| eval TrueClientIP="222.205.40.26"
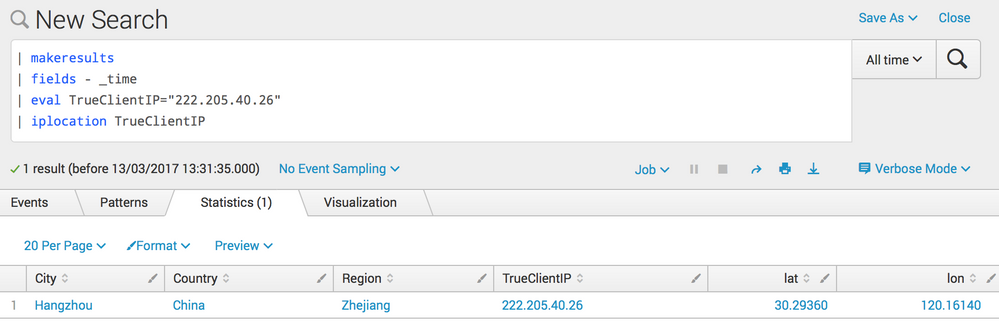
You can then pipe the results to the iplocation command, which will lookup that latitude and longitude:
| iplocation TrueClientIP
Which returns:
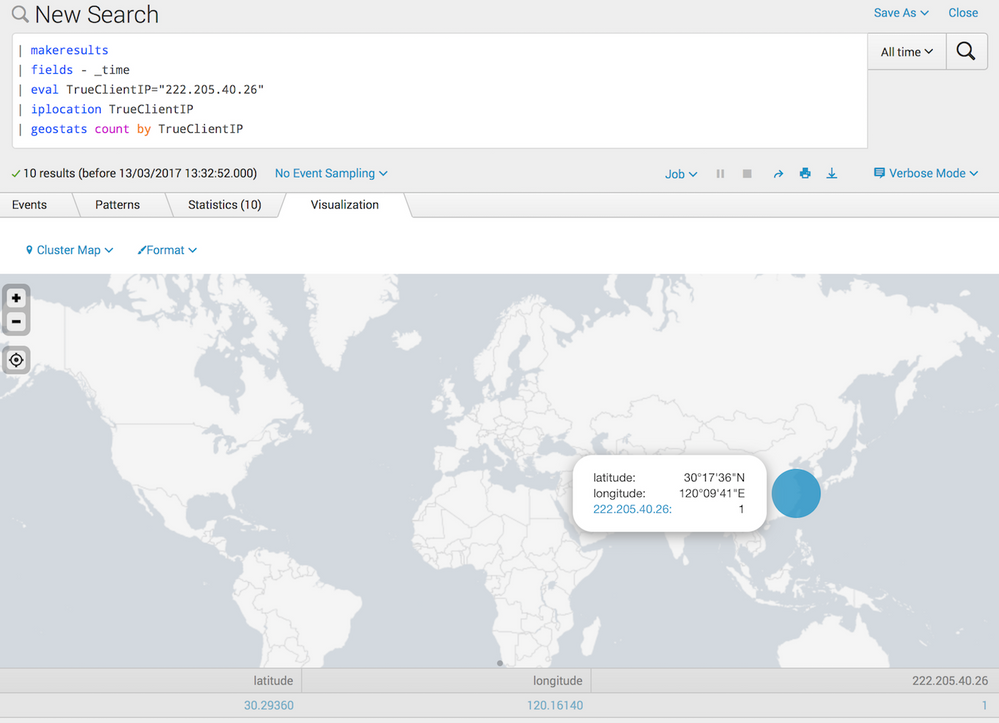
Then pipe this to geostats with the aggregation function. So something like this:
| geostats count by TrueClientIP
If you then go to the Visualization tab and select the 'Cluster Map' chart, you should get something like this:
Have a go with those commands and see how you get on.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
You could try using a combination of iplocation and geostats to generate a report.
Here's an example.
This first part is just to create a result to test with (you'd use the actual data from your search):
| makeresults
| fields - _time
| eval TrueClientIP="222.205.40.26"
You can then pipe the results to the iplocation command, which will lookup that latitude and longitude:
| iplocation TrueClientIP
Which returns:
Then pipe this to geostats with the aggregation function. So something like this:
| geostats count by TrueClientIP
If you then go to the Visualization tab and select the 'Cluster Map' chart, you should get something like this:
Have a go with those commands and see how you get on.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@gvmorley Thank you, I get the results I need, but the Map doesn't work. My search is -- sourcetype=iis CookieData="\"UNKNOWN\"" RedirectTo="\"UNKNOWN\"" TrueClientIP!="\"UNKNOWN\"" TrueClientIP!="\"127.0.0.1\"" -- I can't seem to get his right using the code you have provided, mine seems off (Or it just can’t determine the Public IP location, possibly as I cannot see a Long/Lat field in the Events?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've managed to get this working, but only for 1 IP at a time, which I specify on a dropdown that has a Token assigned - $PublicIP$ - when this is set to the wildcard 'All/*' the search (eval section) does not like this. Here is my amended search;
sourcetype=iis_dominos_online_adv CookieData="\"UNKNOWN\"" RedirectTo="\"UNKNOWN\""
| fields - _time
| eval TrueClientIP=$PublicIP_tkn$
| iplocation TrueClientIP
| geostats count by TrueClientIP
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Sorry for the delayed reply.
If you've got it working for 1 IP, then that's a great start.
My guess it that you may need to amend your search slightly with regards to where you are using the token.
Assuming you select a single IP in your dropdown (for example 1.1.1.1), your eval becomes:
| eval TrueClientIP=1.1.1.1
But if you have an 'All' label, with the value '*', then this mean your eval becomes:
| eval TrueClientIP=*
Since '*' is not an IP address, it's not going to work with the iplocation command.
Perhaps you could use the token in the initial search string. So something like:
sourcetype=iis_dominos_online_adv CookieData="\"UNKNOWN\"" RedirectTo="\"UNKNOWN\"" TrueClientIP=$PublicIP_tkn$
This would then return the single result (assuming the IP from your dropdown is unique), or return multiple results if you select 'All/*'.
See if that gets you a bit closer to what you're looking for.