- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Log clearing not showing up from tstats?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
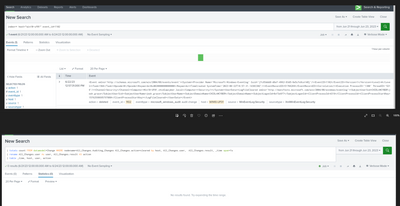
I can search my way into finding the result of a log clearing event bit if I use a data model with tstats it doesn't show. I think this might be because the action shows as action=deleted but the reality is I don't' know.
I am attaching a png of the issue and I and just wondering what is the best way to go about fixing this or changing it so I get it in the way it fits.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
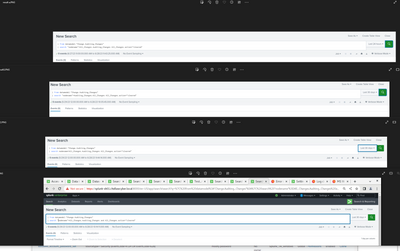
I tried a variety of searches like the ones you see and also added * or replaced cleared with * and got no results.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
you could check what you have on this data model by
| from datamodel:"Change.Auditing_Changes"Then just add needed search after that based what you are looking.
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
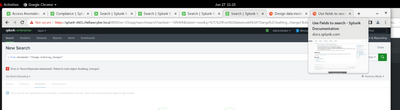
I get the following.
Also where do I go to change things?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
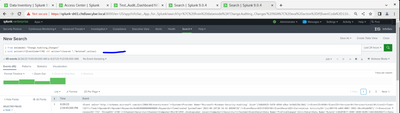
similiar to this or do I make the change else where?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This query shows that you have data on this data model. Now you should add “| search ….” with those search terms which you already have on your first tstats and try to figure if those are present in your DM or are there something which is missing. This is the way to “debug” your tstats from DM.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
which one
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
None of those. I mean your second query on your 1st post. Something like this
| from datamodel:"Change.Auditing_Changes"
| search nodename=All_Changes.Auditing_Changes All_Changes.action=clearedThat way you could found if those fields/values are on your DM or not. Or if you have some typos or other issue on your condition.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am not getting result from that should I be?
now that I have figured out that I am not getinng results in what should I do ?
Also thanks alot for be super clear in your answers as I would not have figured out the exact search part.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Probably this is in wrong order and maybe nodename hasn't defined fields at this time
search nodename=All_Changes.Auditing_ChangesTry to check what you have on fields All_Changes.Auditing_Changes and All_Changes.action.
Also if you want use nodename as a value instead of field you should surround it by " like "nodename" and also cleared as "cleared" if also that is a value.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried a variety of searches like the ones you see and also added * or replaced cleared with * and got no results.