Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Line graph incorrectly shows a flat line
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I have the following search query which shows the output as shown below,as you can see the issue is the linegraph is a flat one when the values are actually different,can anyone provide guidance what is wrong here and how to fix it?
| makeresults
| eval _raw="{
\"entry\" : [{
\"Analyze.Count\":\"100\",
\"Analyze.Screen\":\"100\",
\"Analyze.Investigate\":\"101\",
\"Analyze.Review\":\"103\",
\"_time\": 1556668713
}, {
\"Analyze.Count\":\"700\",
\"Analyze.Screen\":\"800\",
\"Analyze.Investigate\":\"801\",
\"Analyze.Review\":\"803\",
\"_time\": 1556683685
},{
\"Analyze.Count\":\"200\",
\"Analyze.Screen\":\"1000\",
\"Analyze.Investigate\":\"1001\",
\"Analyze.Review\":\"1003\",
\"_time\": 1556683885
},{
\"Analyze.Count\":\"50\",
\"Analyze.Screen\":\"800\",
\"Analyze.Investigate\":\"801\",
\"Analyze.Review\":\"803\",
\"_time\": 1556682885
}]
}"
| spath
| fields - _raw _time
| mvexpand entry{}._time
| rename entry{}.* as *
| timechart min(*) AS * max(*) AS *
CURRENT OUTPUT:-
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The last line of the query is causing the issue, because the min is named the same as the max. So the results are showing the max for each category. Further, using the * will do all the values at the same time. Not sure what you're looking for over time, but assuming it is, then change the last line to something like:
| timechart min(*) AS min_* max(*) AS max_*
or
| stats min(*) AS min_* max(*) AS max_* BY _time
You'll see the result is now giving you the min and max values per field across all the times. It's still a straight line, as that's the min or max from the data set.
If this reply helps you, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The last line of the query is causing the issue, because the min is named the same as the max. So the results are showing the max for each category. Further, using the * will do all the values at the same time. Not sure what you're looking for over time, but assuming it is, then change the last line to something like:
| timechart min(*) AS min_* max(*) AS max_*
or
| stats min(*) AS min_* max(*) AS max_* BY _time
You'll see the result is now giving you the min and max values per field across all the times. It's still a straight line, as that's the min or max from the data set.
If this reply helps you, an upvote would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
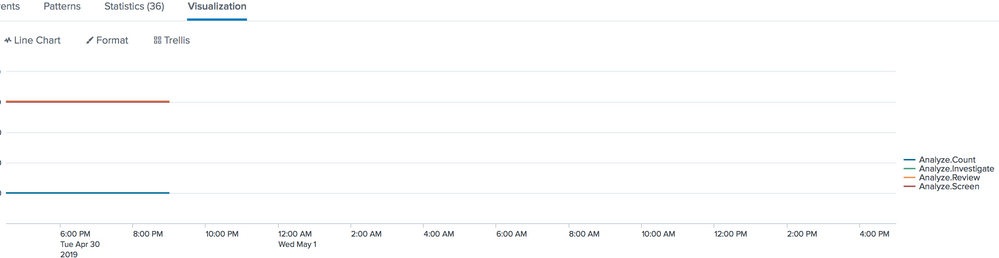
The chart is giving the correct output. have a look at the statistics tab - values are 700,1001,1003 and 1000 for each occurence of Analyze.Count,Analyze.Screen,Analyze.Investigate and Analyze.Review respectively.
For example analyze count has 3 values all equal to 700 and thats what the blue line is showing - a straight line with all values =700
I suspect your requirement is something else...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But statistics is also right,look at the values for Analyze.Count,Analyze.Screen,Analyze.Investigate and Analyze.Review over _time ,they are not the same... Anyways I solved this myself
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@isplunk2999 if you have found a solution to your problem do post the same as answer and accept the same to mark this question as answered and assist others facing similar issue.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And how did you solve it?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @isplunk2999 - The stats generated from your above code is gives only the value 700 for analyze count and that is what the line chart is showing, you probably want all the values Analyze.Count,Analyze.Screen,Analyze.Investigate and Analyze.Review IN a single field, in which case you need to modify your code and have the values 700,1001,1003 and 1000 for one single field.
Anyways, since you have figured out what you needed I guess its ok 🙂