Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Is there a way to nest the last event inside the e...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm attempting to use stats to process some data before further calculations are performed. I have too many events for transaction and would like to "keep" certain data from certain values of foo.
| stats values(eval(if('foo'="bar", A, null()))
The above expression runs, but returns multiple values if there is more than one foo event with different values of A. Sometimes the values are the same for a certain value of foo, but not always. Each field that gets passed through needs mv handling on the other side to get it back down to just one value. That's not ideal as there are 20+ fields that are needed after this stats command. Based on the context of foo I often know whether I want to keep the first or the last value.
The expression
| stats values(eval(case('foo'="bar", A)))
Returns only one value, from the first event where the condition in the case statement is met. However, this doesn't work when what I want is the last occurrence of 'foo'="bar" and not the first.
I've checked the eval+stats documentation and splunk answers, but I'm having trouble finding an example of dynamic fields that uses first() last() earliest() or latest() instead of a sum or count function.
Ideally I'd do something like:
|stats last(eval(if('foo'="bar", A, null()))
Which would return the value of A for the last event matching the condition foo="bar". However, if foo="bar" is not the last event then no data is returned.
Is there a way to nest the last inside the eval statement? Should I be looking at match() instead?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ErikaE ,
The last option should work for you or at least this is what I see.
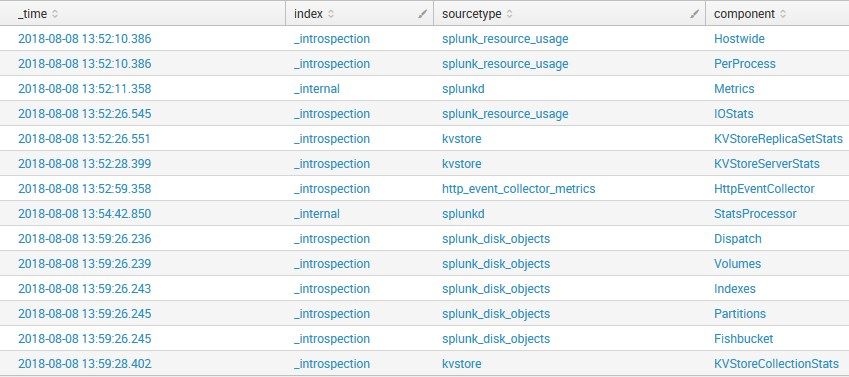
Events
If you see here, the last sourcetype is kvstore and the component is KVStoreCollectionStats
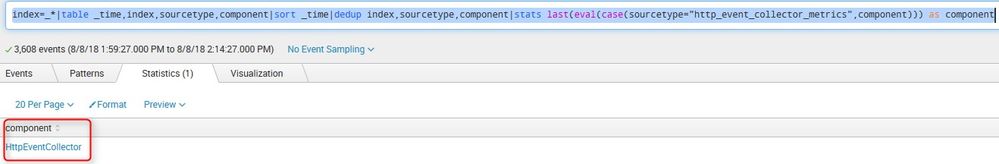
Now here is my SPL
index=_*|table _time,index,sourcetype,component|sort _time|dedup index,sourcetype,component|stats last(eval(case(sourcetype="http_event_collector_metrics",component))) as component
Which yields me the result " HttpEventCollector " which is not in my last event
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ErikaE ,
The last option should work for you or at least this is what I see.
Events
If you see here, the last sourcetype is kvstore and the component is KVStoreCollectionStats
Now here is my SPL
index=_*|table _time,index,sourcetype,component|sort _time|dedup index,sourcetype,component|stats last(eval(case(sourcetype="http_event_collector_metrics",component))) as component
Which yields me the result " HttpEventCollector " which is not in my last event
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I must have had a typo in my syntax somewhere, I'm now seeing the behavior you'd expect.
Thanks for taking the time to look and work up the example for me!