Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Individual results for stats in a chart.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm pretty sure this is going to be very obvious but it's one of those days again.
I've a field Duration_Seconds to establish length of calls going through the system. I'm trying to display say the top 20 longest calls, however, whatever I try, it basis the results on total count, not length.
So even if I have a hundred calls at 30 seconds long that's not what I'm after, I,m after the individual call at 12257 seconds, 10545 seconds, 10140 seconds etc. However, if I have 5 calls at 900 seconds, I still need to see those as separate instances.
Does that make sense?
The search I'm using is:
host=*|search Code_Dialled=9 Duration_Seconds=* |sort - "Duration_Seconds"
which gives me it as a search, it's the last bit I'm stumped on.
Thanks again,
Stu..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
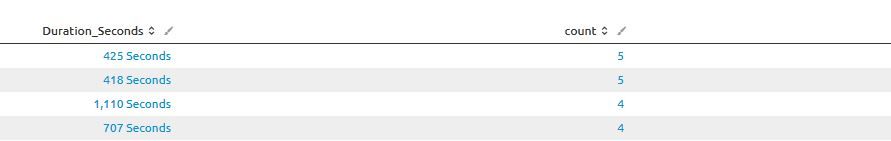
Hi thanks for getting back. It gives pretty much what i already have. The issue is when I try and chart it say using top 100 "Call_Duration" it goes back to giving me the top number by count, so I have 5 calls at 425 seconds as my number one in the chart. I'd ideally like to show say the top 20 / 50, so if I have 5 calls all at 999, they are all shown as individual calls.
So if I search it give me the below, which is perfect.
But what I actually get using, say Top 20.... is
Hopefully this makes a little more sense
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi thanks for getting back. It gives pretty much what i already have. The issue is when I try and chart it say using top 100 "Call_Duration" it goes back to giving me the top number by count, so I have 5 calls at 425 seconds as my number one in the chart. I'd ideally like to show say the top 20 / 50, so if I have 5 calls all at 999, they are all shown as individual calls.
So if I search it give me the below, which is perfect.
But what I actually get using, say Top 20.... is
Hopefully this makes a little more sense
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First, when responding to an answer, it is best to put your response as a comment to the answer and not a new answer. Use the "Add comment" link below the answer to do this.
Regarding your question. What do you want on the x-axis of the chart? Do you want time? If not, please clarify.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ooops sorry about that.
Good point on the X axis never thought about that.
It would be a field called Called_Number (not shown on the sample)
So X would be the number they dialled and Y would be the amount of time they spent on that (long) call.
Thanks again,
Stu..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then try this search.
host=* Code_Dialled=9 Duration_Seconds=* | sort 20 -"Duration_Seconds | table "Called_Number" "Duration_Seconds"
And play with that in the Search app where you can choose a Column chart.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Brilliant thanks. It needs a little tweaking ( more cosmetic than anything else) but it's sent me down the right path.
I can normally brute force my way when learning new systems, but it's nice to have help when you need it and coming from a non-db / programming backgrounding, this forum is a great help thanks to the contribrutors.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is what I think you want. Note, your search pipeline segment should be moved to the first part of the query. Here is what i mean.
host=* Code_Dialled=9 Duration_Seconds=* | sort 20 -"Duration_Seconds"